「TCG 规范解读」第11章 TPM工作组 TCG算法注册表

可信计算组织(Ttrusted Computing Group,TCG)是一个非盈利的工业标准组织,它的宗旨是加强在相异计算机平台上的计算环境的安全性。TCG于2003年春成立,并采纳了由可信计算平台联盟(the Trusted Computing Platform Alliance,TCPA)所开发的规范。现在的规范都不是最终稿,都还在不断的更新中,比如:TPM的规范就从原来的v1.0更新到v1.2,现在还在不断的修订。
TCG-_Algorithm_Registry_r1p32_pub
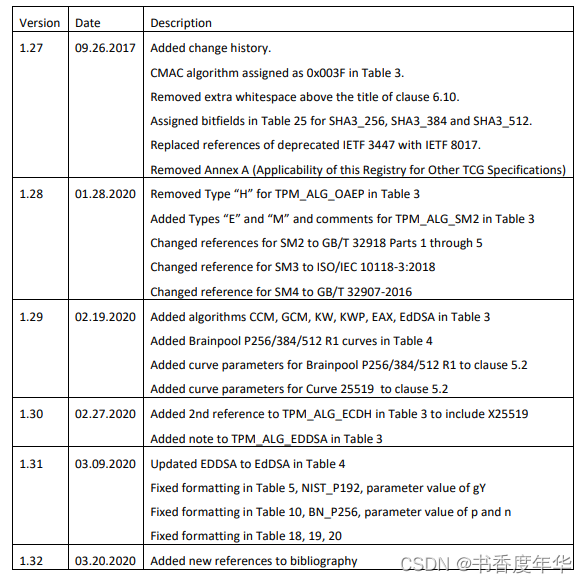
修订历史
TPM_ALG_ID
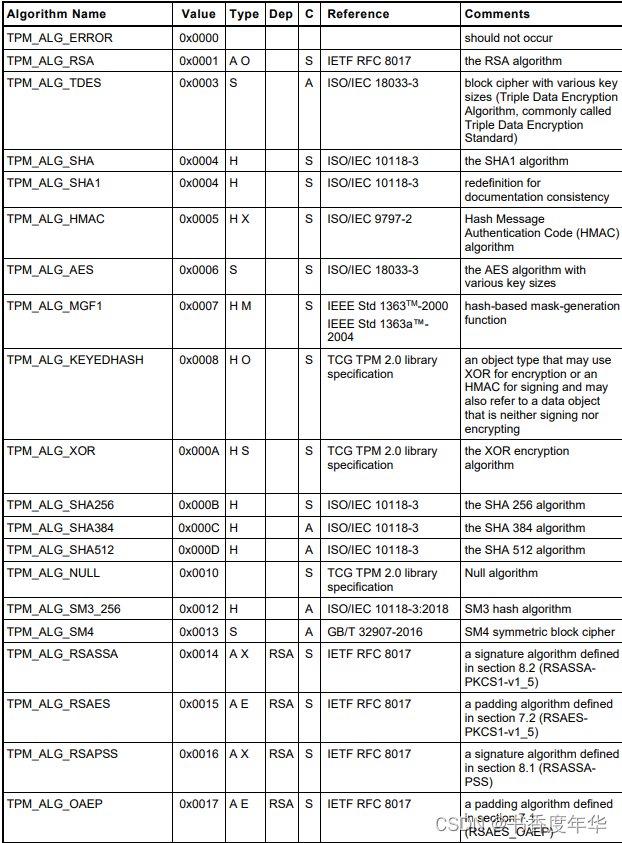
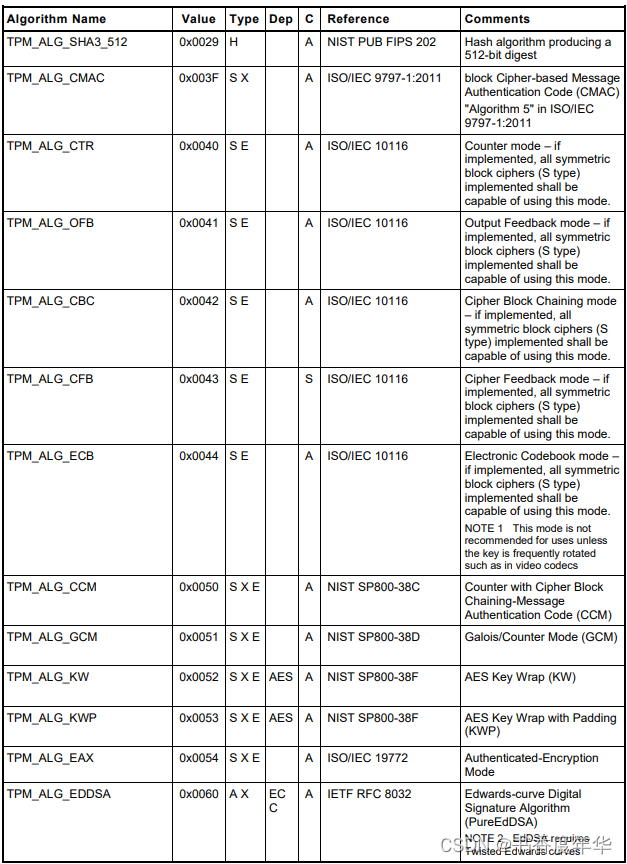
表3 是 TCG 给各个算法分配的标识,这些 ID 可用用来区分算法上下文中的数据结构,合法 ID 的取值范围是 0x0000~0x7fff,0x8000 以上用做 TCG 规定的其他的标签值。
这些算法包含了 RSA、TDES、SHA、HMAC、AES、SM3、SM4、ECC、KDF等,看起来是非常丰富的算法支持。其中 SM3、SM4 是国密算法,这也是 TPM 2.0 中引入的支持。
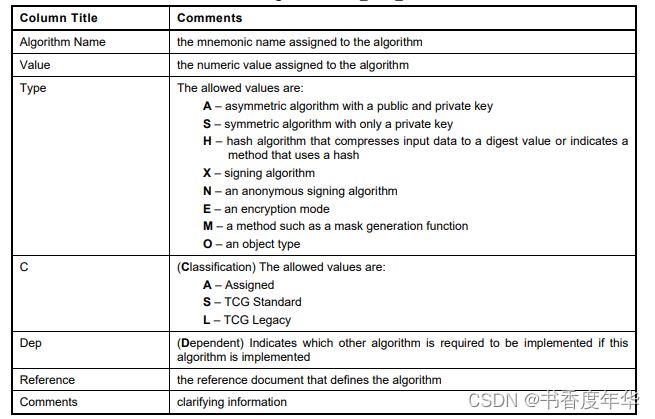
从表2中我们可以看到算法名称、表示的数值、算法类型、依赖、类别、参考以及备注。
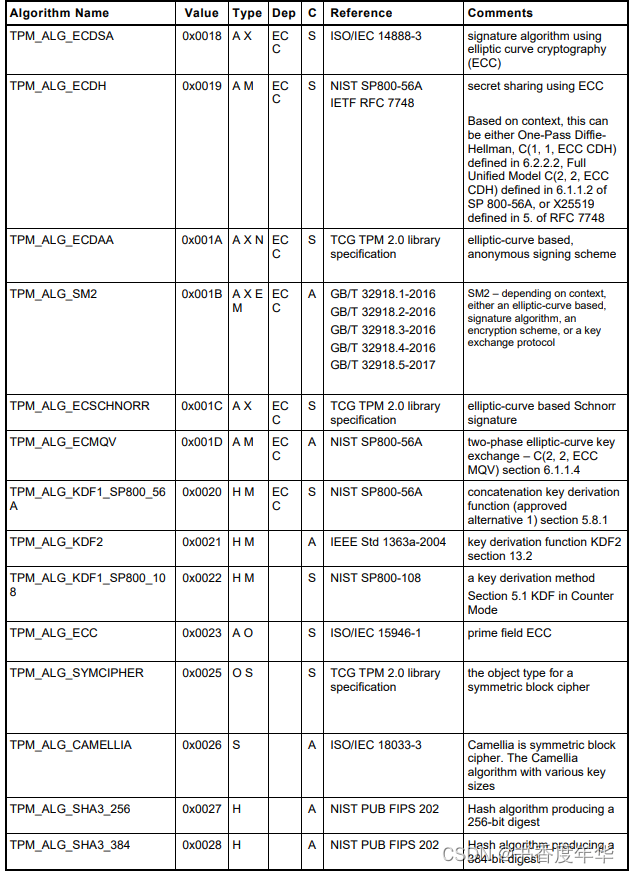
ECC相关数值
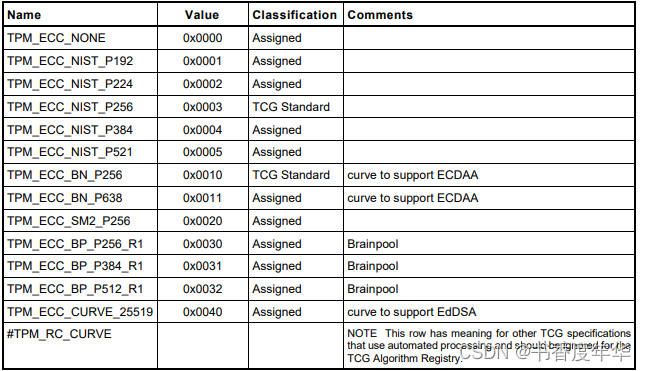
算法 ID
表 5 列出了 TCG 注册的 ECC 算法的 ID,可以看出对于 ECC 的支持也是比较全面的,包含了NIST 系列曲线、BN 曲线、SM2 曲线、BP 曲线、25519 曲线。
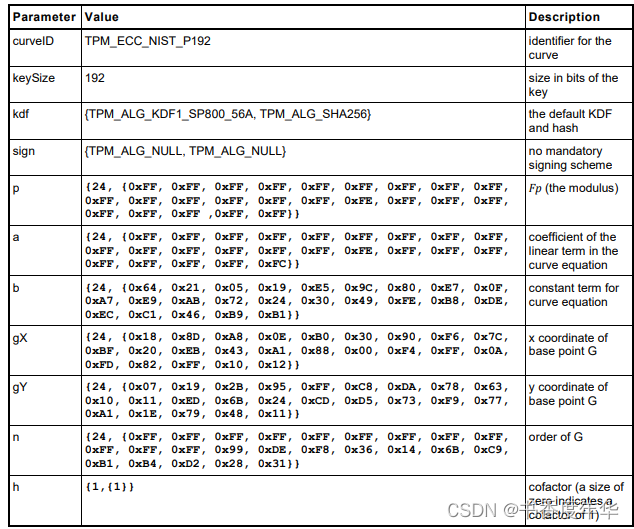
曲线参数
这节主要描述了图 5 中描述 ECC 算法的相关参数,具体如下:
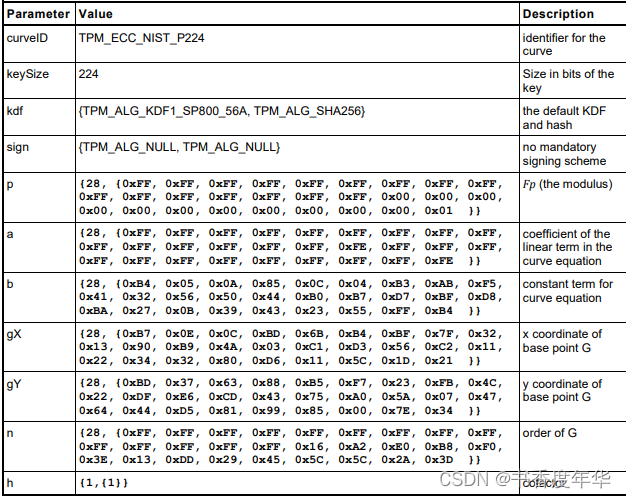
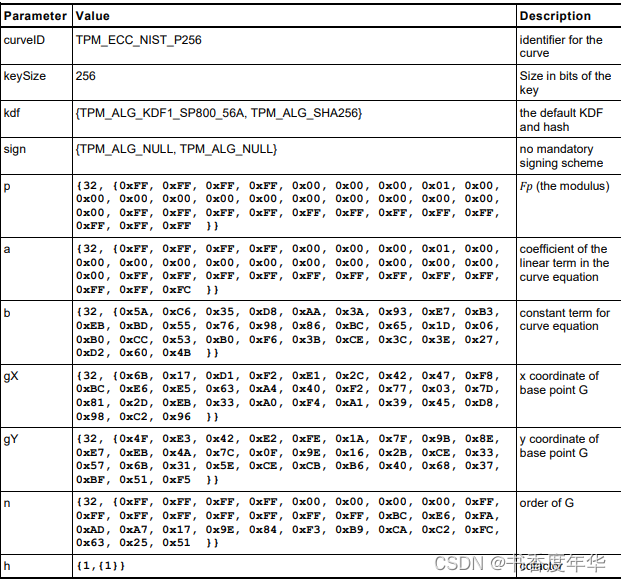
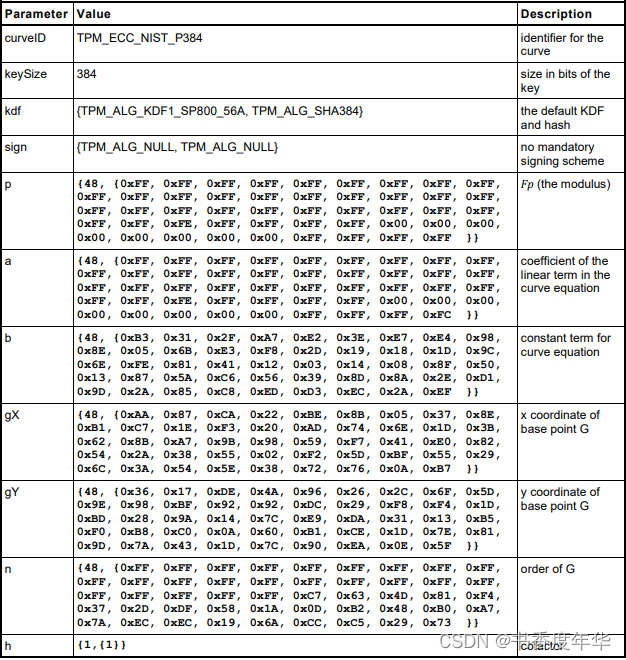
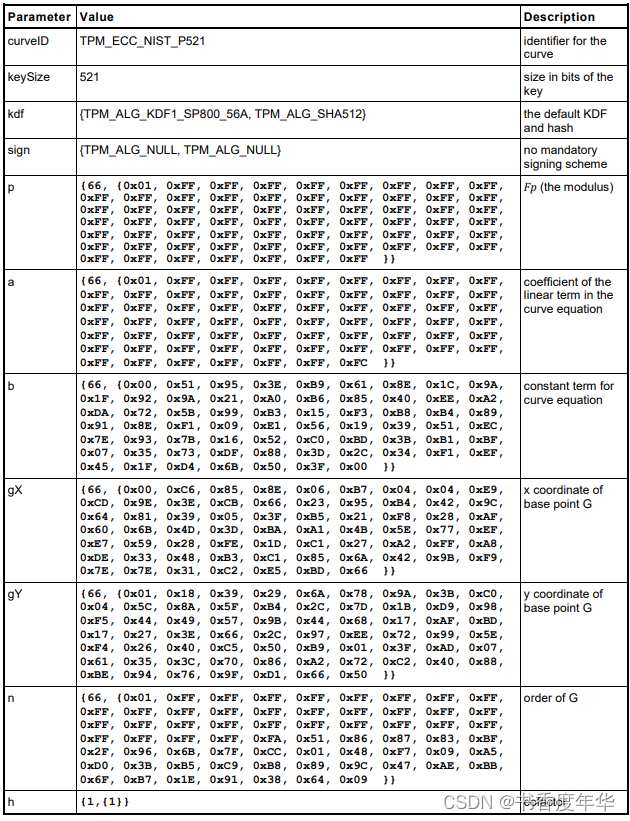
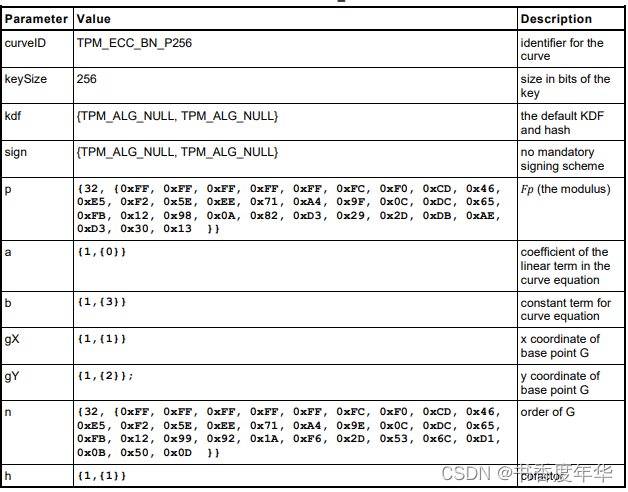
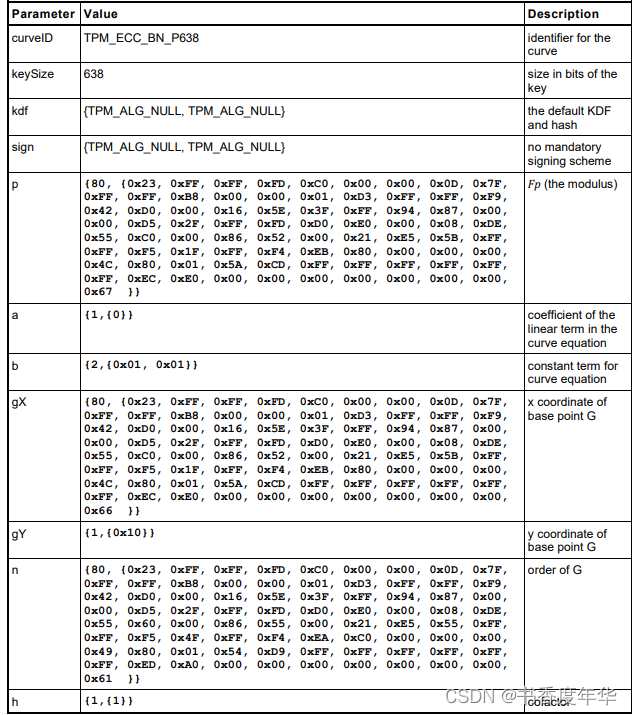
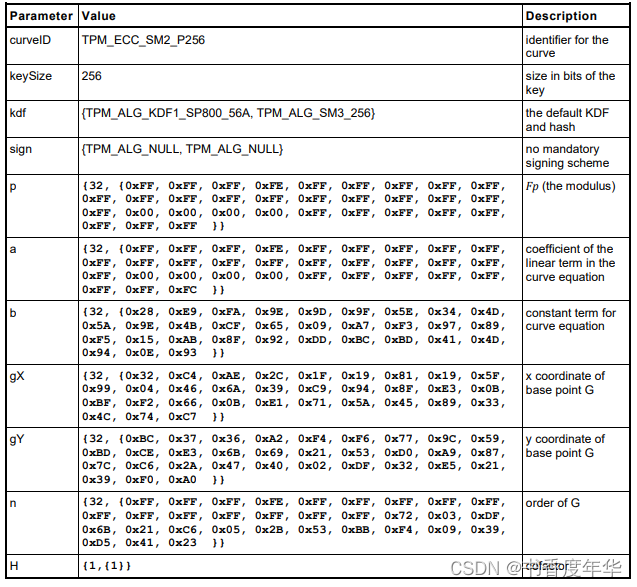
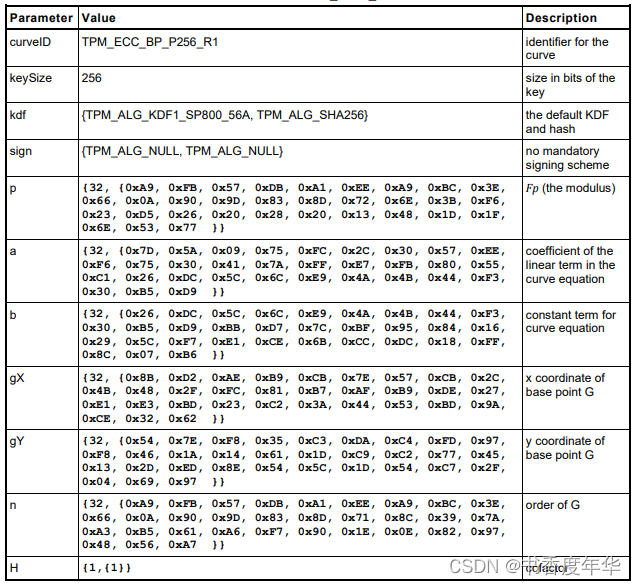
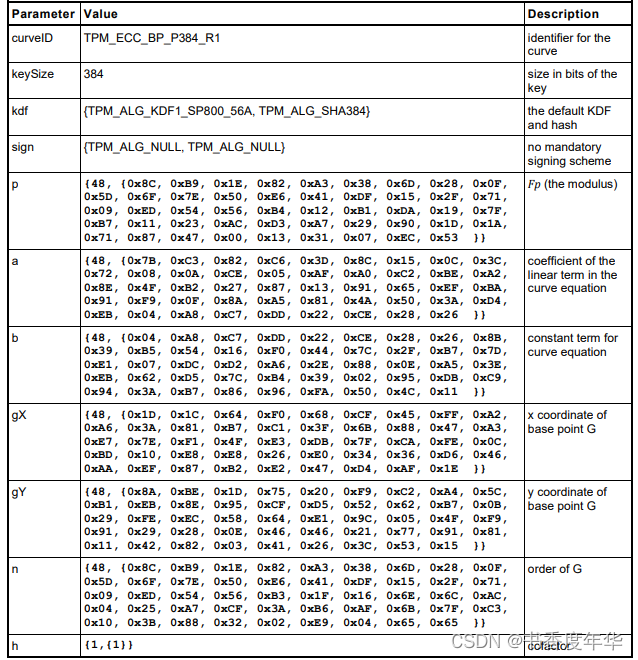
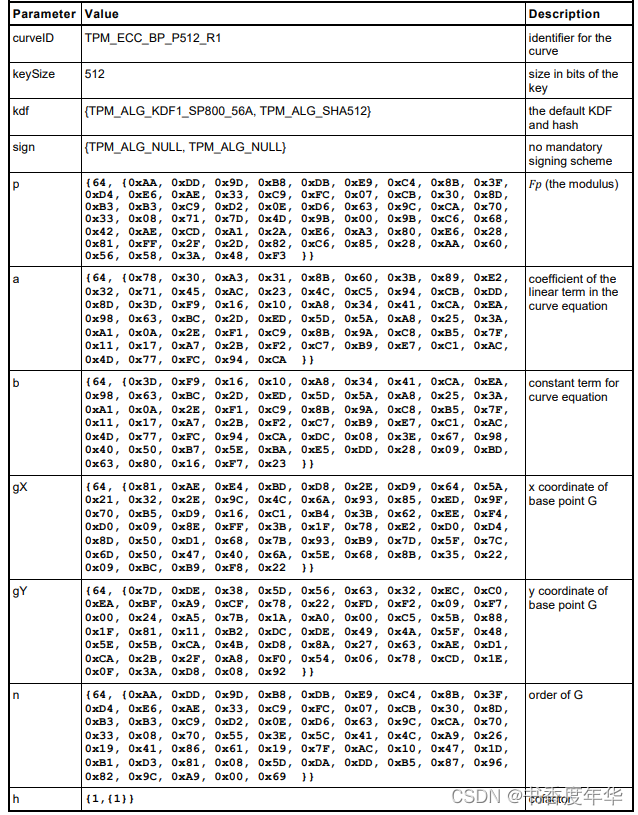
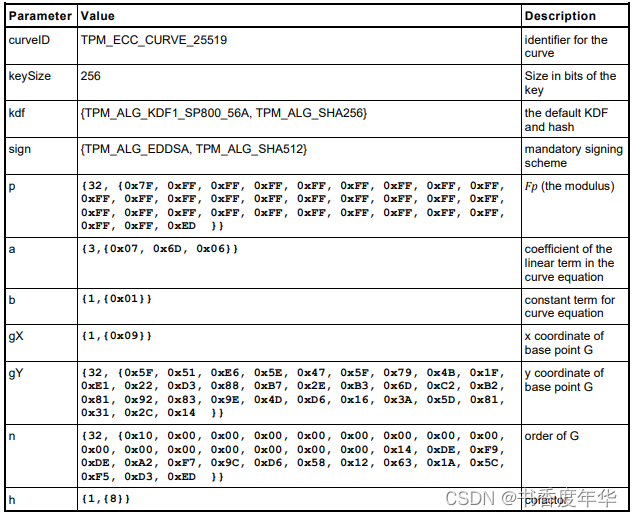
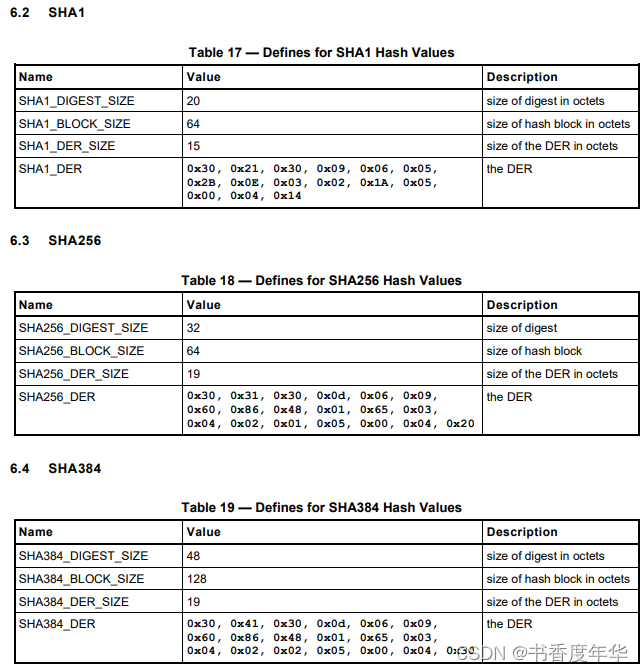
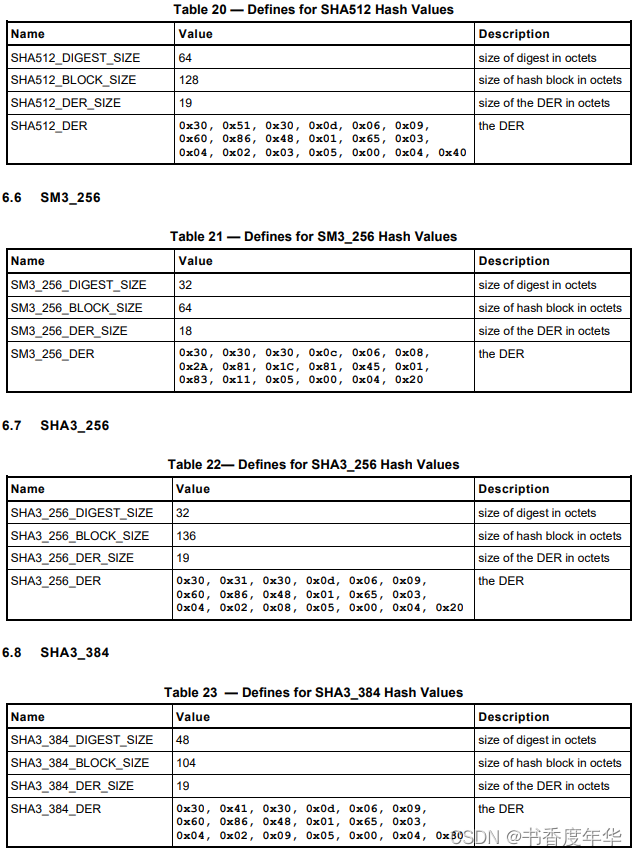
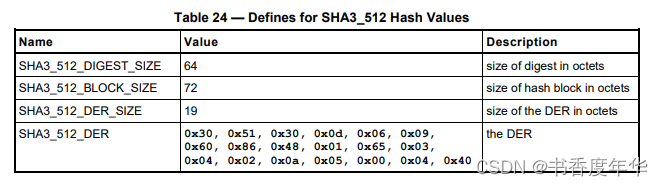
哈希参数
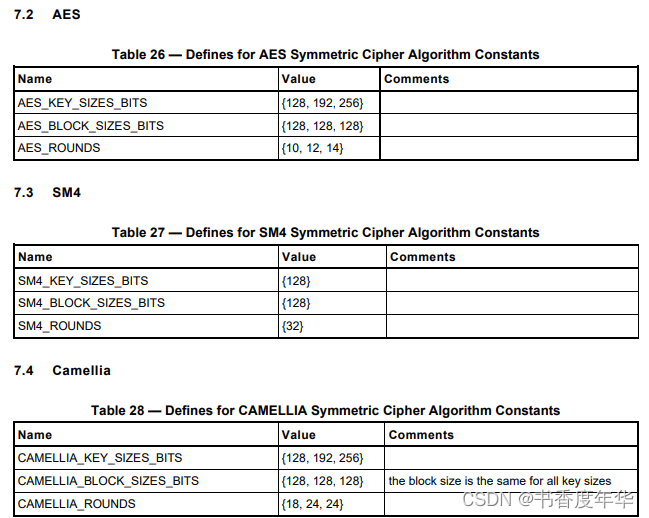
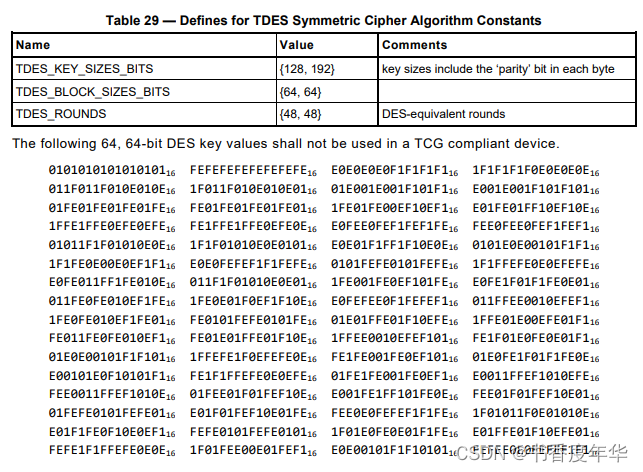
对称加密参数
参考
• FIPS 202, SHA-3 Standard: Permutation-Based Hash and Extendable-Output Functions
• GB/T 32907-2016: Information security technology—SM4 block cipher algorithm
• GB/T 32918.1-2016: Information security technology—Public key cryptographic algorithm SM2 based on elliptic curves—Part 1: General
• GB/T 32918.2-2016: Information security technology—Public key cryptographic algorithm SM2 based on elliptic curves—Part 2: Digital signature algorithm
• GB/T 32918.3-2016: Information security technology—Public key cryptographic algorithm SM2 based on elliptic curves—Part 3: Key exchange protocol
• GB/T 32918.4-2016: Information security technology—Public key cryptographic algorithm SM2 based on elliptic curves—Part 4: Public key encryption algorithm
• GB/T 32918.5-2017: Information security technology—Public key cryptographic algorithm SM2 based on elliptic curves—Part 5: Parameter definition
• IEEE Std 1363TM-2000, Standard Specifications for Public Key Cryptography
• IEEE Std 1363a™-2004 (Amendment to IEEE Std 1363™-2000), IEEE Standard Specifications for Public Key Cryptography- Amendment 1: Additional Techniques
• IETF RFC 8017, Public-Key Cryptography Standards (PKCS) #1: RSA Cryptography Specifications Version 2.2
• IETF RFC 7748, Elliptic Curves for Security • IETF RFC 8032, Edwards-Curve Digital Signature Algorithm (EdDSA)
• ISO/IEC 9797-2, Information technology — Security techniques — Message authentication codes (MACs) — Part 2: Mechanisms using a dedicated hash-function
• ISO/IEC 10116, Information technology — Security techniques — Modes of operation for an nbit block cipher
• ISO/IEC 10118-3, Information technology — Security techniques — Hash-functions — Part 3: Dedicated hash functions
• ISO/IEC 14888-3, Information technology -- Security techniques -- Digital signature with appendix -- Part 3: Discrete logarithm based mechanisms
• ISO/IEC 15946-1, Information technology — Security techniques — Cryptographic techniques based on elliptic curves — Part 1: General
• ISO/IEC 18033-3, Information technology — Security techniques — Encryption algorithms — Part 3: Block ciphers
• ISO/IEC 19772, Information technology — Security techniques — Authenticated encryption • NIST SP800-108, Recommendation for Key Derivation Using Pseudorandom Functions (Revised)
• NIST SP800-56A, Recommendation for Pair-Wise Key Establishment Schemes Using Discrete Logarithm Cryptography (Revised)
• NIST SP800-38C, Recommendation for Block Cipher Modes of Operation: The CCM Mode for Authentication and Confidentiality
• NIST SP800-38D, Recommendation for Block Cipher Modes of Operation: Galois/Counter Mode (GCM) and GMAC
术语
TCG,可信计算组织;
TPM,可信平台模块;
可信度量,主体通过密码学方法对客体进行度量的方法;
皮格马利翁效应心理学指出,赞美、赞同能够产生奇迹,越具体,效果越好~
“收藏夹吃灰”是学“器”练“术”非常聪明的方法,帮助我们避免日常低效的勤奋~
