《Kubernetes部署篇:Ubuntu20.04基于containerd二进制部署K8S 1.24.12集群(一主多从)》

一、架构图
如下图所示:
如下图所示:
二、环境信息
1、部署规划
| 主机名 | IP地址 | 操作系统 | 内核版本 | 软件 | 说明 |
|---|---|---|---|---|---|
| etcd01 | 192.168.1.62 | Ubuntu 20.04.5 LTS | 5.15.0-69-generic | ||
| etcd02 | 192.168.1.63 | Ubuntu 20.04.5 LTS | 5.15.0-69-generic | ||
| etcd03 | 192.168.1.64 | Ubuntu 20.04.5 LTS | 5.15.0-69-generic | ||
| k8s-master-62 | 192.168.1.65 | Ubuntu 20.04.5 LTS | 5.15.0-69-generic | ||
| k8s-worker-66 | 192.168.1.66 | Ubuntu 20.04.5 LTS | 5.15.0-69-generic |
2、软件信息
三、初始化环境
四、创建CA证书和私钥
4.1、安装cfssl工具集
#1、下载文件
root@k8s-master-65:/opt# cd /opt/ssl/
root@k8s-master-65:/opt/ssl# wget https://github.com/cloudflare/cfssl/releases/download/v1.6.3/cfssl_1.6.3_linux_amd64
root@k8s-master-65:/opt/ssl# wget https://github.com/cloudflare/cfssl/releases/download/v1.6.3/cfssljson_1.6.3_linux_amd64
root@k8s-master-65:/opt/ssl# wget https://github.com/cloudflare/cfssl/releases/download/v1.6.3/cfssl-certinfo_1.6.3_linux_amd64#2、复制文件
root@k8s-master-65:/opt/ssl# cp cfssl_1.6.3_linux_amd64 /usr/local/bin/cfssl
root@k8s-master-65:/opt/ssl# cp cfssl-certinfo_1.6.3_linux_amd64 /usr/local/bin/cfssl-certinfo
root@k8s-master-65:/opt/ssl# cp cfssljson_1.6.3_linux_amd64 /usr/local/bin/cfssljson#3、添加文件权限
root@k8s-master-65:/opt/ssl# chmod +x /usr/local/bin/cfssl
root@k8s-master-65:/opt/ssl# chmod +x /usr/local/bin/cfssl-certinfo
root@k8s-master-65:/opt/ssl# chmod +x /usr/local/bin/cfssljson
4.2、准备CA配置文件和签名请求
4.2.1、创建配置文件
root@k8s-master-65:/opt/ssl# mkdir ca && cd /opt/ssl/ca
root@k8s-master-65:/opt/ssl/ca# vim ca-config.json
{"signing": {"default": {"expiry": "876000h"},"profiles": {"kubernetes": {"usages": ["signing","key encipherment","server auth","client auth"],"expiry": "876000h"},"kcfg": {"usages": ["signing","key encipherment","client auth"],"expiry": "876000h"}}}
}
4.2.2、创建证书签名请求文件
root@k8s-master-65:/opt/ssl/ca# vim ca-csr.json
{"CN": "kubernetes-ca","key": {"algo": "rsa","size": 2048},"names": [{"C": "CN","ST": "HangZhou","L": "XS","O": "k8s","OU": "System"}],"ca": {"expiry": "876000h"}
}
4.1、生成CA证书和私钥
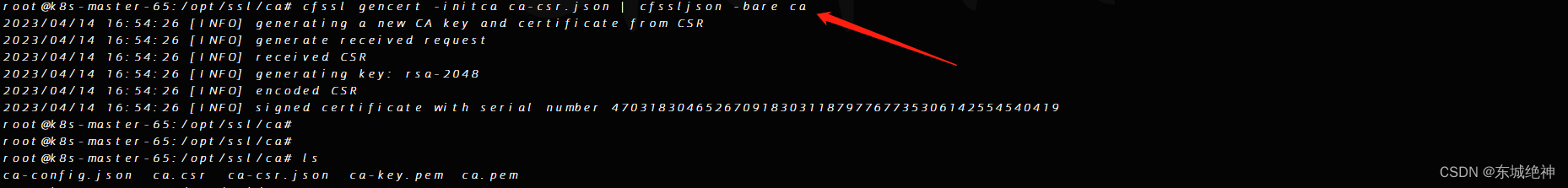
root@k8s-master-65:/opt/ssl/ca# cfssl gencert -initca ca-csr.json | cfssljson -bare ca
如下图所示:
五、部署etcd集群
5.1、创建etcd证书和私钥
5.1.1、创建证书签名请求
root@k8s-master-65:/opt/ssl# mkdir etcd && cd /opt/ssl/etcd
root@k8s-master-65:/opt/ssl/etcd# vim etcd-csr.json
{"CN": "etcd","hosts": ["192.168.1.62","192.168.1.63","192.168.1.64", "127.0.0.1"],"key": {"algo": "rsa","size": 2048},"names": [{"C": "CN","ST": "HangZhou","L": "XS","O": "k8s","OU": "System"}]
}
注意:这里的IP地址一定要根据自己的实际etcd集群ip填写;不然有可能会出现error “remote error: tls: bad certificate”, ServerName ""的错误。
5.1.2、生成证书和私钥
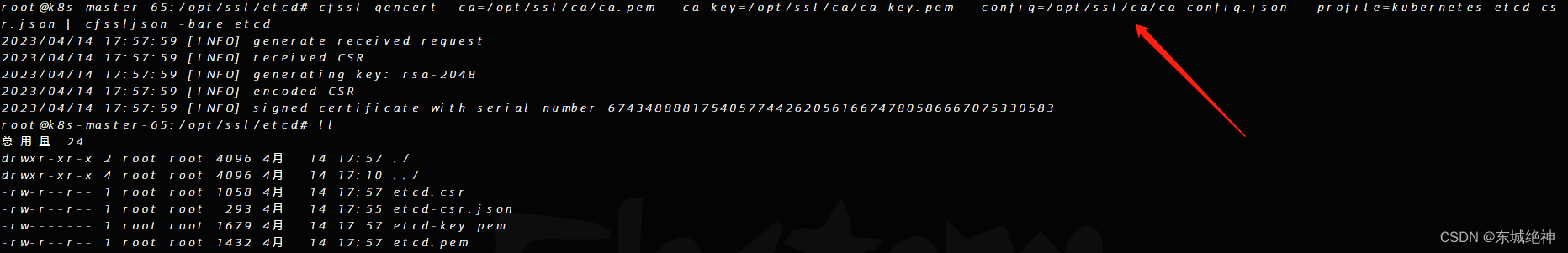
root@k8s-master-65:/opt/ssl/etcd# cfssl gencert -ca=/opt/ssl/ca/ca.pem -ca-key=/opt/ssl/ca/ca-key.pem \\-config=/opt/ssl/ca/ca-config.json -profile=kubernetes etcd-csr.json | cfssljson -bare etcd
如下图所示:
5.1.3、分发证书和私钥至各etcd节点
1、分别在etcd节点创建证书存放目录
#1、在节点etcd01上创建ca证书目录和etcd证书目录
root@etcd01:~# mkdir /etc/kubernetes/ssl -p
root@etcd01:~# mkdir /etc/kubernetes/ssl/etcd -p#2、在节点etcd02上创建ca证书目录和etcd证书目录
root@etcd02:~# mkdir /etc/kubernetes/ssl -p
root@etcd02:~# mkdir /etc/kubernetes/ssl/etcd -p#3、在节点etcd03上创建ca证书目录和etcd证书目录
root@etcd03:~# mkdir /etc/kubernetes/ssl -p
root@etcd03:~# mkdir /etc/kubernetes/ssl/etcd -p
2、将ca证书分别拷贝到各etcd节点
root@k8s-master-65:/opt/ssl# scp ca/ca.pem root@192.168.1.62:/etc/kubernetes/ssl
root@k8s-master-65:/opt/ssl# scp ca/ca.pem root@192.168.1.63:/etc/kubernetes/ssl
root@k8s-master-65:/opt/ssl# scp ca/ca.pem root@192.168.1.64:/etc/kubernetes/ssl
3、将etcd证书分别拷贝到各etcd节点
root@k8s-master-65:/opt/ssl# scp etcd/{etcd.pem,etcd-key.pem} root@192.168.1.62:/etc/kubernetes/ssl/etcd
root@k8s-master-65:/opt/ssl# scp etcd/{etcd.pem,etcd-key.pem} root@192.168.1.63:/etc/kubernetes/ssl/etcd
root@k8s-master-65:/opt/ssl# scp etcd/{etcd.pem,etcd-key.pem} root@192.168.1.64:/etc/kubernetes/ssl/etcd
总结:整理不易,如果对你有帮助,可否点赞关注一下?
更多详细内容请参考:企业级K8s集群运维实战
